PEN-300 Tip - Saving AppLocker Policy
A brief tutorial on how to save yourself some time if needing to reapply AppLocker policies to the lab VMs while doing PEN-300.
I've been working on the PEN-300 courseware over the past ~5 months or so. I was fortunate enough to get a free LearnOne subscription through work. I'd say tl;dr I'm actually surprised with how fun the course has been. I actually may be enjoying it more than PEN-200/OSCP.
One of the areas I thought I could write about are random pain points I experienced in the course - not a product of the courseware - but more so just the nature of the beast. I'm not going to be sharing any of the courseware out of fear of nastygrams. One of these pain points is updating the AppLocker policy on a Windows 10 System.
The course walks you through how to enable AppLocker, so I'll assume you can reference that - or the larger internet - on how to enable the AppLocker policy. What we'll cover here, is how to export the policy - first via PowerShell, and also via the GUI. I've had to do this section over the course of a few days, and each day I've had to spawn a new set of VMs. After the second or third time of manually setting these policies, I found a way to streamline it and thought I would share the process to help others save time. Please note, these instructions are for a Windows 10 system.
PowerShell
Exporting AppLocker Policy via PowerShell
Assuming you have an AppLocker policy set, run from an administrative PowerShell session. You may name the file anything you want, and save it anywhere, but I thought I would save it to my Kali samba share for easy reference.
Get-AppLockerPolicy -Xml -Effective > \\192.168.1.20\visualstudio\files\reg.xmlNote: I mention running from an administrative powershell session because that was what the documentation online stated. However, see the output below of the two files - one run in a regular powershell session (reg.xml), and one run from an admin powershell session (admin.xml). Both are the same file.
Get-FileHash -Algorithm MD5 *.xml
Algorithm Hash Path
--------- ---- ----
MD5 42FF29389B791C52A2F9A3E214FE1013 C:\Users\student\admin.xml
MD5 42FF29389B791C52A2F9A3E214FE1013 C:\Users\student\reg.xmlImport AppLocker Policy via PowerShell
Instead of using the Get-AppLockerPolicy , we'll use the Set-AppLockerPolicy (MSDOC). Run from an administrative powershell session - an actual requirement.
# Run from an administrative powershell session (required)
Set-AppLockerPolicy -XMLPolicy \\192.168.1.20\visualstudio\files\applocker_defaultpolicy.xmlAfterwards, don't forget to run gpupdate /force , from PowerShell, or a command prompt.
Local Policy Group Editor (GUI)
Export Policy
Assuming you have an AppLocker policy set, open the Local Policy Group Editor by running gpedit.msc from an administrative command prompt. Navigate to Computer Configuration --> Windows Settings --> Security Settings --> Application Control Policies, and right click on AppLocker, and select Export Policy.... Name the file, and click OK. A message box will appear sharing the number of policies which were exported successfully.
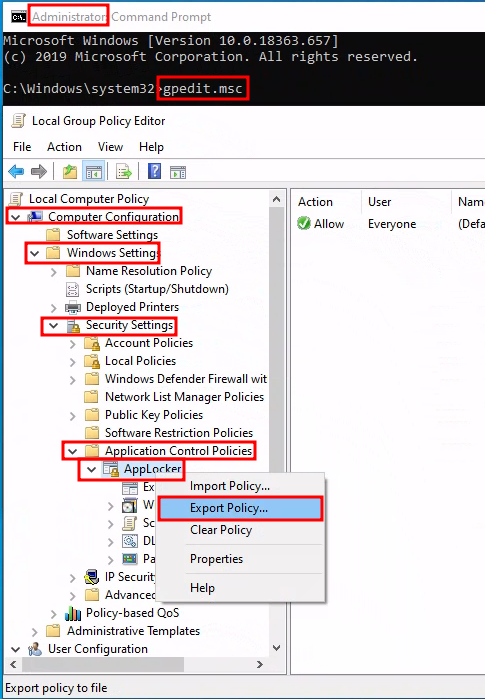
Import Policy
Follow the same steps to find the AppLocker User rules as provided in the Export Policy section. However, instead of choosing Export Policy... select Import Policy.... Navigate to the location of the saved AppLocker policy. A warning message may appear prompting you that Importing a policy will permanently replace all existing policy rules. Click Yes to import and overwrite all the policy rules. Be sure to run gpupdate /force from PowerShell/command line.
Conclusion
Thats it! Simple enough, not earth shattering stuff. However, I wanted to share to hopefully make your OSEP journey slightly easier if at all.